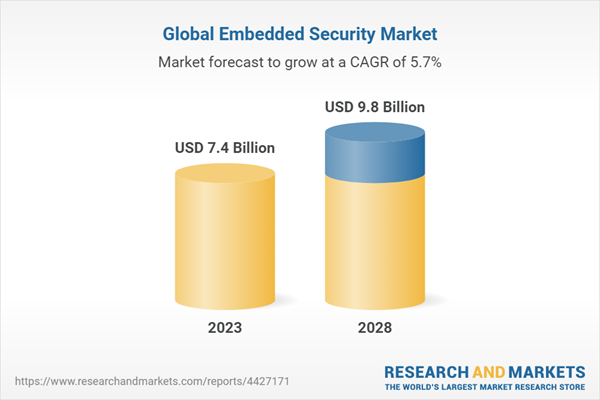
5 Market Overview
5.1 Introduction
5.2 Market Dynamics
Figure 22 Embedded Security Market: Drivers, Restraints, Opportunities and Challenges
5.2.1 Drivers
5.2.1.1 Growing IoT Applications
5.2.1.2 Inclusion of Payments Functionality in Wearables
5.2.1.3 Growing Adoption of Generative AI in Various Applications
5.2.1.4 Digitalization Initiatives by Governments Worldwide
5.2.1.5 Increase in Data Breaches and Cyberattacks
5.2.1.6 Rising Demand for Robust Security Solutions for Electric and Hybrid Vehicles
5.2.1.7 Need for More Secure Crypto-based Transactions
5.2.2 Restraints
5.2.2.1 Non-Compliance with Government Regulations due to Lack of Auditing
5.2.2.2 Susceptibility of Embedded Systems to Cyberthreats and Security Breaches
5.2.2.3 Inclination of Customers Toward Renting Hardware Security Modules
5.2.3 Opportunities
5.2.3.1 Integration of Embedded Security in Electric Vehicles
5.2.3.2 Growing Importance of IoT Security in Development of Smart Cities
5.2.3.3 Growing Adoption of Embedded Security in Healthcare Systems
5.2.3.4 Emergence of 5G and Advancements in 5G-Enabled Embedded Devices
5.2.4 Challenges
5.2.4.1 Lack of Safety Awareness Regarding Embedded Systems and Limited Security Budget
5.2.4.2 High Energy Consumption Associated with Compact Embedded Systems
5.2.4.3 Designing Complexities Associated with Embedded Systems
5.2.4.4 Shortage in Supply of Semiconductors
5.3 Value Chain Analysis
Figure 23 Embedded Security Market: Value Chain Analysis
5.4 Ecosystem Mapping
Table 2 Participants and Their Role in Ecosystem
Figure 24 Participants in Embedded Security Ecosystem
5.5 Revenue Shifts and New Revenue Pockets for Players in Embedded Security Market
Figure 25 Trends and Disruptions Impacting Customer Business
5.6 Technology Trends
5.6.1 Growing Emphasis on Automobile Security
5.6.2 Increasing Contactless Payment
5.6.3 Rising Use of Wearables
5.6.4 Increasing Number of IoT Devices
5.6.5 Emergence of 5G
5.7 Pricing Analysis
Table 3 Indicative Pricing Analysis of Embedded Security Hardware Components
5.8 Porter's Five Forces Analysis
Table 4 Embedded Security Market: Porter's Five Forces Analysis, 2022
Figure 26 Embedded Security Market: Porter's Five Forces Analysis
Figure 27 Embedded Security Market: Impact Analysis of Porter's Five Forces
5.8.1 Bargaining Power of Suppliers
5.8.2 Bargaining Power of Buyers
5.8.3 Threat of New Entrants
5.8.4 Threat of Substitutes
5.8.5 Intensity of Competitive Rivalry
5.9 Case Study Analysis
Table 5 Embedded Security Strengthened Data Protection of Medical Testing Equipment
Table 6 Garuda Indonesia Developed Corporate Mobility Management System to Work on Electronic Flight Bags for Pilots
Table 7 US-based Financial Services Company Created Public Key Infrastructure Inventory Using Venafi Platform
Table 8 Kaspersky Lab and Be.Services GmbH Developed Embedded Security Shield to Safeguard Industrial Control Systems
Table 9 Healthcare Organization Protected Employee Safety and Security with Washable, RFID-Embedded Keyboard
5.10 Trade Analysis
5.10.1 Export Scenario for HS Code 8471, by Country, 2018-2022
Table 10 Export Data for Automatic Data Processing Machines for HS Code 8471, by Country, 2018-2022 (USD Billion)
Figure 28 Export Scenario for Automatic Data Processing Machines for HS Code 8471, by Country, 2018-2022 (USD Billion)
5.10.2 Import Scenario for HS Code 8471, by Country, 2018-2022
Table 11 Import Data for Automatic Data Processing Machines for HS Code 8471, by Country, 2018-2022 (USD Billion)
Figure 29 Import Scenario for Automatic Data Processing Machines for HS Code 8471, by Country, 2018-2022 (USD Billion)
5.11 Patent Analysis
Figure 30 Number of Patents Granted Per Year, 2013-2022
Table 12 Top 10 Patent Owners in Embedded Security Market
Figure 31 Top 10 Companies with Highest Number of Patent Applications in Last 10 Years
5.11.1 List of Major Patents, 2019-2023
Table 13 Embedded Security Market: Patent Registrations, 2019-2023
5.12 Key Stakeholders and Buying Criteria
5.12.1 Key Stakeholders in Buying Process
Figure 32 Influence of Stakeholders on Buying Process, by Offering
Table 14 Influence of Stakeholders on Buying Process, by Offering (%)
5.12.2 Buying Criteria
Figure 33 Key Buying Criteria for Offerings
Table 15 Key Buying Criteria, by Offering
5.13 Key Conferences and Events, 2023-2024
Table 16 Embedded Security Market: List of Conferences and Events
5.14 Tariffs and Regulatory Landscape
5.14.1 Tariffs
5.14.2 Regulatory Bodies, Government Agencies, and Other Organizations
5.14.2.1 North America
5.14.2.2 Europe
5.14.2.3 Asia-Pacific
5.14.2.4 RoW
5.14.3 Standards
Table 17 Base Standards for Information Security
Table 18 European Telecommunications Standards Institute: Standards
5.14.4 Regulations
5.14.4.1 Global
5.14.4.2 North America
5.14.4.3 Europe
5.14.4.4 Asia-Pacific
6 Embedded Security Market, by Security Type
6.1 Introduction
Figure 34 Embedded Security Market, by Security Type, 2023-2028 (USD Million)
Table 19 Embedded Security Market, by Security Type, 2019-2022 (USD Million)
Table 20 Embedded Security Market, by Security Type, 2023-2028 (USD Million)
6.2 Authentication & Access Management
6.2.1 Ability to Block Unauthorized Users from Accessing Devices to Generate Demand for Authentication & Access Management
Table 21 Authentication & Access Management: Embedded Security Market, by Region, 2019-2022 (USD Million)
Table 22 Authentication & Access Management: Embedded Security Market, by Region, 2023-2028 (USD Million)
6.3 Payments
6.3.1 Need to Ensure Secure Transactions and Protect Sensitive Consumer Data to Fuel Demand for Payment Security
Table 23 Payment: Embedded Security Market, by Region, 2019-2022 (USD Million)
Table 24 Payment: Embedded Security Market, by Region, 2023-2028 (USD Million)
6.4 Content Protection
6.4.1 Need to Protect Sensitive Organizational Data from Fraudulent Activities and Privacy Breaches to Drive Market for Content Protection
Table 25 Content Protection: Embedded Security Market, by Region, 2019-2022 (USD Million)
Table 26 Content Protection: Embedded Security Market, by Region, 2023-2028 (USD Million)
7 Embedded Security Market, by Offering
7.1 Introduction
Figure 35 Embedded Security Market, by Offering, 2023-2028 (USD Million)
Table 27 Embedded Security Market, by Offering, 2019-2022 (USD Million)
Table 28 Embedded Security Market, by Offering, 2023-2028 (USD Million)
7.2 Hardware
Table 29 Hardware: Embedded Security Market, by Product, 2019-2022 (USD Million)
Table 30 Hardware: Embedded Security Market, by Product, 2023-2028 (USD Million)
Table 31 Hardware: Embedded Security Market, by Region, 2019-2022 (USD Million)
Table 32 Hardware: Embedded Security Market, by Region, 2023-2028 (USD Million)
7.2.1 Secure Elements
7.2.1.1 Extensive Use of Secure Elements in e-Government Applications such as e-Passports and Smart Identity Cards to Drive Market
7.2.2 Embedded Sim
7.2.2.1 Increasing Machine-to-Machine Connections Globally to Propel Market
7.2.3 Trusted Platform Modules
7.2.3.1 Increasing Number of Cybersecurity Attacks to Fuel Market Growth
7.2.4 Hardware Security Modules
7.2.4.1 Rising Need for Information and Data Security to Drive Market
7.2.5 Hardware Tokens
7.2.5.1 Rising Demand for Secure Internet-based Transactions to Propel Market
7.3 Software
Table 33 Software: Embedded Security Market, by Region, 2019-2022 (USD Million)
Table 34 Software: Embedded Security Market, by Region, 2023-2028 (USD Million)
7.3.1 Firewalls
7.3.1.1 Need to Prevent Unauthorized Computer and Network Access to Boost Adoption of Firewalls
7.3.2 Antivirus
7.3.2.1 Potential to Address Post-Firewall Intrusions and Mitigate Advanced Threats to Contribute to Market Growth
7.3.3 Antispyware
7.3.3.1 Utilization in Monitoring and Detecting Unauthorized Communications to Propel Market
7.3.4 Network Security
7.3.4.1 Higher Cost-Efficiency of Implementing Security at Network Level to Boost Market
7.4 Services
Table 35 Services: Embedded Security Market, by Region, 2019-2022 (USD Million)
Table 36 Services: Embedded Security Market, by Region, 2023-2028 (USD Million)
7.4.1 System Integration Services
7.4.1.1 Increasing Emphasis on Enhancing Quality of Business Operations to Propel Market
7.4.2 Support and Maintenance Services
7.4.2.1 Increased Technological Complexities to Fuel Demand for Support and Maintenance Services
7.4.3 Security Consulting
7.4.3.1 Focus on Enhancing Effectiveness of Business and IT Processes to Boost Demand for Security Consulting
8 Embedded Security Market, by Application
8.1 Introduction
Figure 36 Embedded Security Market, by Application, 2023-2028 (USD Million)
Table 37 Embedded Security Market, by Application, 2019-2022 (USD Million)
Table 38 Embedded Security Market, by Application, 2023-2028 (USD Million)
8.2 Wearables
8.2.1 Rising Integration of Wearable Devices with Digital Wallets to Increase Demand for Embedded Security
Table 39 Wearables: Embedded Security Market, by Region, 2019-2022 (USD Million)
Table 40 Wearables: Embedded Security Market, by Region, 2023-2028 (USD Million)
8.3 Smartphones
8.3.1 Surge in Mobile Payments to Necessitate Adoption of Embedded Security
Table 41 Smartphones: Embedded Security Market, by Region, 2019-2022 (USD Million)
Table 42 Smartphones: Embedded Security Market, by Region, 2023-2028 (USD Million)
8.4 Automotive
8.4.1 Growing Demand for Connected Cars to Boost Market
Table 43 Automotive: Embedded Security Market, by Region, 2019-2022 (USD Million)
Table 44 Automotive: Embedded Security Market, by Region, 2023-2028 (USD Million)
8.5 Smart Identity Cards
8.5.1 Emergence of Multi-Application Smart Cards for Shared Storage and Information Processing to Foster Market Growth
Table 45 Smart Identity Cards: Embedded Security Market, by Region, 2019-2022 (USD Million)
Table 46 Smart Identity Cards: Embedded Security Market, by Region, 2023-2028 (USD Million)
8.6 Industrial
8.6.1 Rising Integration of IoT with Industrial Systems to Support Market Growth
Table 47 Industrial: Embedded Security Market, by Region, 2019-2022 (USD Million)
Table 48 Industrial: Embedded Security Market, by Region, 2023-2028 (USD Million)
8.7 Payment Processing & Cards
8.7.1 Increasing e-Commerce Sales and Growing Internet Penetration to Spur Market Growth
Table 49 Payment Processing & Cards: Embedded Security Market, by Region, 2019-2022 (USD Million)
Table 50 Payment Processing & Cards: Embedded Security Market, by Region, 2023-2028 (USD Million)
8.8 Others
Table 51 Others: Embedded Security Market, by Region, 2019-2022 (USD Million)
Table 52 Others: Embedded Security Market, by Region, 2023-2028 (USD Million)
9 Embedded Security Market, by Region
9.1 Introduction
Figure 37 Embedded Security Market, by Country
Table 53 Embedded Security Market, by Region, 2019-2022 (USD Million)
Table 54 Embedded Security Market, by Region, 2023-2028 (USD Million)
9.2 North America
Figure 38 North America: Embedded Security Market Snapshot
9.2.1 Recession Impact on Embedded Security Market in North America
Figure 39 North America: Recession Impact Analysis, 2019-2028
Table 55 North America: Embedded Security Market, by Security Type, 2019-2022 (USD Million)
Table 56 North America: Embedded Security Market, by Security Type, 2023-2028 (USD Million)
Table 57 North America: Embedded Security Market, by Offering, 2019-2022 (USD Million)
Table 58 North America: Embedded Security Market, by Offering, 2023-2028 (USD Million)
Table 59 North America: Embedded Security Market, by Application, 2019-2022 (USD Million)
Table 60 North America: Embedded Security Market, by Application, 2023-2028 (USD Million)
Table 61 North America: Embedded Security Market, by Country, 2019-2022 (USD Million)
Table 62 North America: Embedded Security Market, by Country, 2023-2028 (USD Million)
9.2.2 US
9.2.2.1 Rising Cost Burden of Data Breaches to Fuel Demand for Embedded Security
Table 63 US: Embedded Security Market, by Security Type, 2019-2022 (USD Million)
Table 64 US: Embedded Security Market, by Security Type, 2023-2028 (USD Million)
Table 65 US: Embedded Security Market, by Offering, 2019-2022 (USD Million)
Table 66 US: Embedded Security Market, by Offering, 2023-2028 (USD Million)
Table 67 US: Embedded Security Market, by Application, 2019-2022 (USD Million)
Table 68 US: Embedded Security Market, by Application, 2023-2028 (USD Million)
9.2.3 Canada
9.2.3.1 Rapid Advancements in Next-Generation Digital Technologies to Foster Market Growth
Table 69 Canada: Embedded Security Market, by Security Type, 2019-2022 (USD Million)
Table 70 Canada: Embedded Security Market, by Security Type, 2023-2028 (USD Million)
Table 71 Canada: Embedded Security Market, by Offering, 2019-2022 (USD Million)
Table 72 Canada: Embedded Security Market, by Offering, 2023-2028 (USD Million)
Table 73 Canada: Embedded Security Market, by Application, 2019-2022 (USD Million)
Table 74 Canada: Embedded Security Market, by Application, 2023-2028 (USD Million)
9.2.4 Mexico
9.2.4.1 Rising Adoption of Wireless Connectivity Technologies to Contribute to Market Growth
Table 75 Mexico: Embedded Security Market, by Security Type, 2019-2022 (USD Million)
Table 76 Mexico: Embedded Security Market, by Security Type, 2023-2028 (USD Million
Table 77 Mexico: Embedded Security Market, by Offering, 2019-2022 (USD Million)
Table 78 Mexico: Embedded Security Market, by Offering, 2023-2028 (USD Million)
Table 79 Mexico: Embedded Security Market, by Application, 2019-2022 (USD Million)
Table 80 Mexico: Embedded Security Market, by Application, 2023-2028 (USD Million)
9.3 Europe
Figure 40 Europe: Embedded Security Market Snapshot
9.3.1 Recession Impact on Embedded Security Market in Europe
Figure 41 Europe: Recession Impact Analysis, 2019-2028
Table 81 Europe: Embedded Security Market, by Security Type, 2019-2022 (USD Million)
Table 82 Europe: Embedded Security Market, by Security Type, 2023-2028 (USD Million)
Table 83 Europe: Embedded Security Market, by Offering, 2019-2022 (USD Million)
Table 84 Europe: Embedded Security Market, by Offering, 2023-2028 (USD Million)
Table 85 Europe: Embedded Security Market, by Application, 2019-2022 (USD Million)
Table 86 Europe: Embedded Security Market, by Application, 2023-2028 (USD Million)
Table 87 Europe: Embedded Security Market, by Country, 2019-2022 (USD Million)
Table 88 Europe: Embedded Security Market, by Country, 2023-2028 (USD Million)
9.3.2 UK
9.3.2.1 Sharp Increase in Cyberattacks to Boost Demand for Embedded Security Systems
Table 89 UK: Embedded Security Market, by Security Type, 2019-2022 (USD Million)
Table 90 UK: Embedded Security Market, by Security Type, 2023-2028 (USD Million)
Table 91 UK: Embedded Security Market, by Offering, 2019-2022 (USD Million)
Table 92 UK: Embedded Security Market, by Offering, 2023-2028 (USD Million)
Table 93 UK: Embedded Security Market, by Application, 2019-2022 (USD Million)
Table 94 UK: Embedded Security Market, by Application, 2023-2028 (USD Million)
9.3.3 Germany
9.3.3.1 Rising Government Investments in Security Projects to Fuel Market Growth
Table 95 Germany: Embedded Security Market, by Security Type, 2019-2022 (USD Million)
Table 96 Germany: Embedded Security Market, by Security Type, 2023-2028 (USD Million)
Table 97 Germany: Embedded Security Market, by Offering, 2019-2022 (USD Million)
Table 98 Germany: Embedded Security Market, by Offering, 2023-2028 (USD Million)
Table 99 Germany: Embedded Security Market, by Application, 2019-2022 (USD Million)
Table 100 Germany: Embedded Security Market, by Application, 2023-2028 (USD Million)
9.3.4 France
9.3.4.1 Increasing Initiatives to Boost Cybersecurity to Accelerate Market Growth
Table 101 France: Embedded Security Market, by Security Type, 2019-2022 (USD Million)
Table 102 France: Embedded Security Market, by Security Type, 2023-2028 (USD Million)
Table 103 France: Embedded Security Market, by Offering, 2019-2022 (USD Million)
Table 104 France: Embedded Security Market, by Offering, 2023-2028 (USD Million)
Table 105 France: Embedded Security Market, by Application, 2019-2022 (USD Million)
Table 106 France: Embedded Security Market, by Application, 2023-2028 (USD Million)
9.3.5 Rest of Europe
Table 107 Rest of Europe: Embedded Security Market, by Security Type, 2019-2022 (USD Million)
Table 108 Rest of Europe: Embedded Security Market, by Security Type, 2023-2028 (USD Million)
Table 109 Rest of Europe: Embedded Security Market, by Offering, 2019-2022 (USD Million)
Table 110 Rest of Europe: Embedded Security Market, by Offering, 2023-2028 (USD Million)
Table 111 Rest of Europe: Embedded Security Market, by Application, 2019-2022 (USD Million)
Table 112 Rest of Europe: Embedded Security Market, by Application, 2023-2028 (USD Million)
9.4 Asia-Pacific
Figure 42 Asia-Pacific: Embedded Security Market Snapshot
9.4.1 Recession Impact on Embedded Security Market in Asia-Pacific
Figure 43 Asia-Pacific: Recession Impact Analysis, 2019-2028
Table 113 Asia-Pacific: Embedded Security Market, by Security Type, 2019-2022 (USD Million)
Table 114 Asia-Pacific: Embedded Security Market, by Security Type, 2023-2028 (USD Million)
Table 115 Asia-Pacific: Embedded Security Market, by Offering, 2019-2022 (USD Million)
Table 116 Asia-Pacific: Embedded Security Market, by Offering, 2023-2028 (USD Million)
Table 117 Asia-Pacific: Embedded Security Market, by Application, 2019-2022 (USD Million)
Table 118 Asia-Pacific: Embedded Security Market, by Application, 2023-2028 (USD Million)
Table 119 Asia-Pacific: Embedded Security Market, by Country, 2019-2022 (USD Million)
Table 120 Asia-Pacific: Embedded Security Market, by Country, 2023-2028 (USD Million)
9.4.2 China
9.4.2.1 Enforcement of Data Management and Security Laws to Boost Market Growth
Table 121 China: Embedded Security Market, by Security Type, 2019-2022 (USD Million)
Table 122 China: Embedded Security Market, by Security Type, 2023-2028 (USD Million)
Table 123 China: Embedded Security Market, by Offering, 2019-2022 (USD Million)
Table 124 China: Embedded Security Market, by Offering, 2023-2028 (USD Million)
Table 125 China: Embedded Security Market, by Application, 2019-2022 (USD Million)
Table 126 China: Embedded Security Market, by Application, 2023-2028 (USD Million)
9.4.3 South Korea
9.4.3.1 5G Implementation to Boost Demand for Embedded Security Solutions
Table 127 South Korea: Embedded Security Market, by Security Type, 2019-2022 (USD Million)
Table 128 South Korea: Embedded Security Market, by Security Type, 2023-2028 (USD Million)
Table 129 South Korea: Embedded Security Market, by Offering, 2019-2022 (USD Million)
Table 130 South Korea: Embedded Security Market, by Offering, 2023-2028 (USD Million)
Table 131 South Korea: Embedded Security Market, by Application, 2019-2022 (USD Million)
Table 132 South Korea: Embedded Security Market, by Application, 2023-2028 (USD Million)
9.4.4 Japan
9.4.4.1 Government Focus on Strengthening Cybersecurity Capabilities to Boost Market Growth
Table 133 Japan: Embedded Security Market, by Security Type, 2019-2022 (USD Million)
Table 134 Japan: Embedded Security Market, by Security Type, 2023-2028 (USD Million)
Table 135 Japan: Embedded Security Market, by Offering, 2019-2022 (USD Million)
Table 136 Japan: Embedded Security Market, by Offering, 2023-2028 (USD Million)
Table 137 Japan: Embedded Security Market, by Application, 2019-2022 (USD Million)
Table 138 Japan: Embedded Security Market, by Application, 2023-2028 (USD Million)
9.4.5 Rest of Asia-Pacific
Table 139 Rest of Asia-Pacific: Embedded Security Market, by Security Type, 2019-2022 (USD Million)
Table 140 Rest of Asia-Pacific: Embedded Security Market, by Security Type, 2023-2028 (USD Million)
Table 141 Rest of Asia-Pacific: Embedded Security Market, by Offering, 2019-2022 (USD Million)
Table 142 Rest of Asia-Pacific: Embedded Security Market, by Offering, 2023-2028 (USD Million)
Table 143 Rest of Asia-Pacific: Embedded Security Market, by Application, 2019-2022 (USD Million)
Table 144 Rest of Asia-Pacific: Embedded Security Market, by Application, 2023-2028 (USD Million)
9.5 RoW
9.5.1 Recession Impact on Embedded Security Market in RoW
Figure 44 RoW: Recession Impact Analysis, 2019-2028
Table 145 RoW: Embedded Security Market, by Security Type, 2019-2022 (USD Million)
Table 146 RoW: Embedded Security Market, by Security Type, 2023-2028 (USD Million)
Table 147 RoW: Embedded Security Market, by Offering, 2019-2022 (USD Million)
Table 148 RoW: Embedded Security Market, by Offering, 2023-2028 (USD Million)
Table 149 RoW: Embedded Security Market, by Application, 2019-2022 (USD Million)
Table 150 RoW: Embedded Security Market, by Application, 2023-2028 (USD Million)
Table 151 RoW: Embedded Security Market, by Region, 2019-2022 (USD Million)
Table 152 RoW: Embedded Security Market, by Region, 2023-2028 (USD Million)
9.5.2 Middle East & Africa
9.5.2.1 Rising Focus on Ensuring Cyber Resilience in Oil & Gas Sector to Boost Market
9.5.3 Latin America
9.5.3.1 Increasing Investment in Transportation and Energy Infrastructure to Propel Market
10 Competitive Landscape
10.1 Introduction
10.2 Strategies Adopted by Key Players, 2020-2023
Table 153 Overview of Strategies Adopted by Key Players, 2020-2023
10.3 Revenue Analysis of Key Players, 2018-2022
Figure 45 5-Year Revenue Analysis of Key Players in Embedded Security Market
10.4 Market Share Analysis, 2022
Table 154 Embedded Security Market: Degree of Competition
Figure 46 Market Share Analysis, 2022
10.5 Key Company Evaluation Matrix, 2022
10.5.1 Stars
10.5.2 Pervasive Players
10.5.3 Emerging Leaders
10.5.4 Participants
Figure 47 Embedded Security Market: Key Company Evaluation Matrix, 2022
10.6 Competitive Benchmarking of Key Players
Table 155 Overall Company Footprint
Table 156 Company Footprint, by Application
Table 157 Company Footprint, by Offering
Table 158 Company Footprint, by Region
10.7 Small and Medium-Sized Enterprises (SMEs)/Startups Evaluation Matrix, 2022
10.7.1 Progressive Companies
10.7.2 Responsive Companies
10.7.3 Dynamic Companies
10.7.4 Starting Blocks
Figure 48 Embedded Security Market: SMEs/Startups Evaluation Matrix, 2022
10.8 Competitive Scenarios and Trends
10.8.1 Product Launches
Table 159 Embedded Security Market: Product Launches and Developments, 2021-2023
10.8.2 Deals
Table 160 Embedded Security Market: Deals, 2021-2023
10.9 Competitive Benchmarking of Startups/SMEs
Table 161 Embedded Security Market: List of Key Startups/SMEs
Table 162 Embedded Security Market: Competitive Benchmarking of Key Startups/SMEs
11 Company Profiles
(Business Overview, Products/Solutions/Services Offered, Recent Developments, and Analyst's View (Key Strengths/Right to Win, Strategic Choices Made, and Weaknesses and Competitive Threats))*
11.1 Introduction
11.2 Key Players
11.2.1 Infineon Technologies AG
Table 163 Infineon Technologies AG: Company Overview
Figure 49 Infineon Technologies AG: Company Snapshot
Table 164 Infineon Technologies AG: Products/Solutions/Services Offered
Table 165 Infineon Technologies AG: Product Launches
Table 166 Infineon Technologies AG: Deals
Table 167 Infineon Technologies AG: Others
11.2.2 STMicroelectronics
Table 168 STMicroelectronics: Company Overview
Figure 50 STMicroelectronics: Company Snapshot
Table 169 STMicroelectronics: Products/Solutions/Services Offered
Table 170 STMicroelectronics: Product Launches
Table 171 STMicroelectronics: Deals
11.2.3 NXP Semiconductors
Table 172 NXP Semiconductors: Company Overview
Figure 51 NXP Semiconductors: Company Snapshot
Table 173 NXP Semiconductors: Products/Solutions/Services Offered
Table 174 NXP Semiconductors: Product Launches
Table 175 NXP Semiconductors: Deals
11.2.4 Texas Instruments Incorporated
Table 176 Texas Instruments Incorporated: Company Overview
Figure 52 Texas Instruments Incorporated: Company Snapshot
Table 177 Texas Instruments Incorporated: Products/Solutions/Services Offered
Table 178 Texas Instruments Incorporated: Product Launches
Table 179 Texas Instruments Incorporated: Deals
Table 180 Texas Instruments Incorporated: Others
11.2.5 Qualcomm Technologies, Inc.
Table 181 Qualcomm Technologies, Inc.: Company Overview
Figure 53 Qualcomm Technologies, Inc.: Company Snapshot
Table 182 Qualcomm Technologies, Inc.: Products/Solutions/Services Offered
Table 183 Qualcomm Technologies, Inc.: Product Launches
Table 184 Qualcomm Technologies, Inc.: Deals
11.2.6 Renesas Electronics Corporation
Table 185 Renesas Electronics Corporation: Company Overview
Figure 54 Renesas Electronics Corporation: Company Snapshot
Table 186 Renesas Electronics Corporation: Products/Solutions/Services Offered
Table 187 Renesas Electronics Corporation: Product Launches
Table 188 Renesas Electronics Corporation: Deals
Table 189 Renesas Electronics Corporation: Others
11.2.7 Thales
Table 190 Thales: Company Overview
Figure 55 Thales Group: Company Snapshot
Table 191 Thales: Products/Solutions/Services Offered
Table 192 Thales: Product Launches
Table 193 Thales: Deals
11.2.8 Microchip Technology Inc.
Table 194 Microchip Technology Inc.: Company Overview
Figure 56 Microchip Technology Inc.: Company Snapshot
Table 195 Microchip Technology Inc.: Products/Solutions/Services Offered
Table 196 Microchip Technology Inc.: Product Launches
Table 197 Microchip Technology Inc.: Others
11.2.9 Samsung
Table 198 Samsung: Company Overview
Figure 57 Samsung: Company Snapshot
Table 199 Samsung: Products/Solutions/Services Offered
Table 200 Samsung: Product Launches
11.2.10 IDEMIA
Table 201 IDEMIA: Company Overview
Table 202 IDEMIA: Products/Solutions/Services Offered
Table 203 IDEMIA: Product Launches
Table 204 IDEMIA: Deals
11.2.11 ICTK Co. Ltd.
Table 205 ICTK Co. Ltd.: Company Overview
Table 206 ICTK Co. Ltd.: Products/Solutions/Services Offered
Table 207 ICTK Co. Ltd.: Deals
11.3 Other Players
11.3.1 Rambus Inc.
11.3.2 Cisco Systems, Inc.
11.3.3 ETAS
11.3.4 OVD Kinegram AG
11.3.5 BAE Systems
11.3.6 Lantronix, Inc.
11.3.7 IBM
11.3.8 Swift
11.3.9 McAfee, LLC
11.3.10 Broadcom
11.3.11 HiTex GmbH
11.3.12 Analog Devices, Inc.
11.3.13 Advantech Co. Ltd.
11.3.14 Eta Compute
11.3.15 RunSafe Security
*Details on Business Overview, Products/Solutions/Services Offered, Recent Developments, and Analyst's View (Key Strengths/Right to Win, Strategic Choices Made, and Weaknesses and Competitive Threats) Might Not be Captured in Case of Unlisted Companies