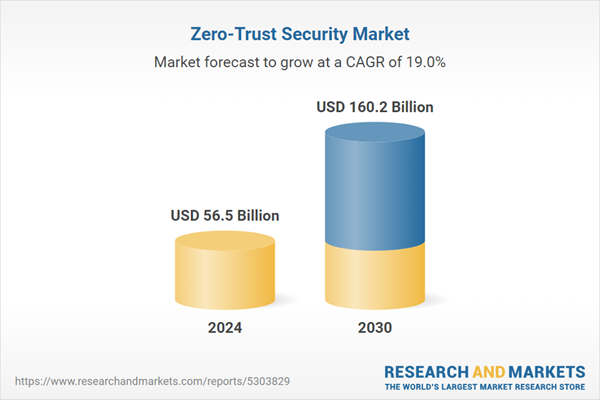
The global market for Zero-Trust Security was valued at US$56.5 Billion in 2024 and is projected to reach US$160.2 Billion by 2030, growing at a CAGR of 19.0% from 2024 to 2030. This comprehensive report provides an in-depth analysis of market trends, drivers, and forecasts, helping you make informed business decisions. The report includes the most recent global tariff developments and how they impact the Zero-Trust Security market.
Escalating frequency and sophistication of cyberattacks represent one of the primary drivers for the adoption of zero-trust security. Organizations are facing constant threats from hackers, ransomware, and other malicious actors who exploit traditional perimeter-based security models. As cyber threats become more advanced, the need for a more robust and comprehensive security framework like zero-trust is imperative. Additionally, regulatory bodies worldwide are enforcing stricter data protection and privacy laws, such as GDPR and CCPA, which mandate stronger security measures to protect sensitive information. Zero-trust security helps organizations comply with these regulations by ensuring continuous monitoring and verification of all access requests.
Advancements in identity and access management (IAM) technologies are also driving the growth of zero-trust security. Modern IAM solutions, such as multi-factor authentication (MFA), single sign-on (SSO), and biometric authentication, provide the foundational elements needed to implement a zero-trust framework effectively. These technologies enhance security by ensuring that only verified users and devices can access sensitive information. Additionally, the integration of artificial intelligence (AI) and machine learning (ML) in IAM solutions allows for real-time analysis and detection of anomalous behavior, further strengthening the zero-trust model. As these technologies continue to evolve, they make the deployment of zero-trust security more feasible and effective for organizations of all sizes. With the increasing reliance on cloud services, Cloud Security Posture Management (CSPM) is expected to become essential in zero trust strategies. CSPM tools help businesses continuously monitor and manage their cloud security posture, ensuring compliance and reducing risks associated with cloud-based vulnerabilities.
Zero Trust is a continually evolving security model, adapting to meet current threats and business needs. The future of Zero Trust will see deeper integration across various security pillars, leading to more streamlined policy automation, advanced threat detection, and comprehensive attack mitigation strategies. The shift towards remote work and the widespread adoption of cloud services have significantly altered the traditional network perimeter, making it more porous and difficult to secure. With employees accessing corporate resources from various locations and devices, and businesses increasingly relying on cloud-based applications and infrastructure, the attack surface has expanded
Segments: Deployment (Cloud, On-Premise); Organization Size (Large Enterprises, SMEs); Vertical (IT & ITES, Financial & Insurance, Healthcare & Social Assistance, Retail Trade, Utilities, Other Verticals).
Geographic Regions/Countries: World; United States; Canada; Japan; China; Europe (France; Germany; Italy; United Kingdom; and Rest of Europe); Asia-Pacific; Rest of World.
The analysts continuously track trade developments worldwide, drawing insights from leading global economists and over 200 industry and policy institutions, including think tanks, trade organizations, and national economic advisory bodies. This intelligence is integrated into forecasting models to provide timely, data-driven analysis of emerging risks and opportunities.
Global Zero-Trust Security Market - Key Trends and Drivers Summarized
Zero-Trust Security is a cybersecurity framework that operates on the principle of 'never trust, always verify.' Unlike traditional security models that assume everything inside an organization's network is safe, zero-trust security requires strict identity verification for every person and device trying to access resources on a private network, regardless of whether they are inside or outside the network perimeter. This approach ensures that only authenticated and authorized users and devices can access applications and data, significantly reducing the risk of data breaches and cyberattacks.Escalating frequency and sophistication of cyberattacks represent one of the primary drivers for the adoption of zero-trust security. Organizations are facing constant threats from hackers, ransomware, and other malicious actors who exploit traditional perimeter-based security models. As cyber threats become more advanced, the need for a more robust and comprehensive security framework like zero-trust is imperative. Additionally, regulatory bodies worldwide are enforcing stricter data protection and privacy laws, such as GDPR and CCPA, which mandate stronger security measures to protect sensitive information. Zero-trust security helps organizations comply with these regulations by ensuring continuous monitoring and verification of all access requests.
Advancements in identity and access management (IAM) technologies are also driving the growth of zero-trust security. Modern IAM solutions, such as multi-factor authentication (MFA), single sign-on (SSO), and biometric authentication, provide the foundational elements needed to implement a zero-trust framework effectively. These technologies enhance security by ensuring that only verified users and devices can access sensitive information. Additionally, the integration of artificial intelligence (AI) and machine learning (ML) in IAM solutions allows for real-time analysis and detection of anomalous behavior, further strengthening the zero-trust model. As these technologies continue to evolve, they make the deployment of zero-trust security more feasible and effective for organizations of all sizes. With the increasing reliance on cloud services, Cloud Security Posture Management (CSPM) is expected to become essential in zero trust strategies. CSPM tools help businesses continuously monitor and manage their cloud security posture, ensuring compliance and reducing risks associated with cloud-based vulnerabilities.
Zero Trust is a continually evolving security model, adapting to meet current threats and business needs. The future of Zero Trust will see deeper integration across various security pillars, leading to more streamlined policy automation, advanced threat detection, and comprehensive attack mitigation strategies. The shift towards remote work and the widespread adoption of cloud services have significantly altered the traditional network perimeter, making it more porous and difficult to secure. With employees accessing corporate resources from various locations and devices, and businesses increasingly relying on cloud-based applications and infrastructure, the attack surface has expanded
Report Scope
The report analyzes the Zero-Trust Security market, presented in terms of units. The analysis covers the key segments and geographic regions outlined below.Segments: Deployment (Cloud, On-Premise); Organization Size (Large Enterprises, SMEs); Vertical (IT & ITES, Financial & Insurance, Healthcare & Social Assistance, Retail Trade, Utilities, Other Verticals).
Geographic Regions/Countries: World; United States; Canada; Japan; China; Europe (France; Germany; Italy; United Kingdom; and Rest of Europe); Asia-Pacific; Rest of World.
Key Insights:
- Market Growth: Understand the significant growth trajectory of the Cloud segment, which is expected to reach US$110.4 Billion by 2030 with a CAGR of a 19.9%. The On-Premise segment is also set to grow at 17.1% CAGR over the analysis period.
- Regional Analysis: Gain insights into the U.S. market, valued at $15.8 Billion in 2024, and China, forecasted to grow at an impressive 17.9% CAGR to reach $24.0 Billion by 2030. Discover growth trends in other key regions, including Japan, Canada, Germany, and the Asia-Pacific.
Why You Should Buy This Report:
- Detailed Market Analysis: Access a thorough analysis of the Global Zero-Trust Security Market, covering all major geographic regions and market segments.
- Competitive Insights: Get an overview of the competitive landscape, including the market presence of major players across different geographies.
- Future Trends and Drivers: Understand the key trends and drivers shaping the future of the Global Zero-Trust Security Market.
- Actionable Insights: Benefit from actionable insights that can help you identify new revenue opportunities and make strategic business decisions.
Key Questions Answered:
- How is the Global Zero-Trust Security Market expected to evolve by 2030?
- What are the main drivers and restraints affecting the market?
- Which market segments will grow the most over the forecast period?
- How will market shares for different regions and segments change by 2030?
- Who are the leading players in the market, and what are their prospects?
Report Features:
- Comprehensive Market Data: Independent analysis of annual sales and market forecasts in US$ Million from 2024 to 2030.
- In-Depth Regional Analysis: Detailed insights into key markets, including the U.S., China, Japan, Canada, Europe, Asia-Pacific, Latin America, Middle East, and Africa.
- Company Profiles: Coverage of players such as Akamai, Centrify, Check Point Software Technologies, Cisco, Cloudflare and more.
- Complimentary Updates: Receive free report updates for one year to keep you informed of the latest market developments.
Some of the 34 companies featured in this Zero-Trust Security market report include:
- Akamai
- Centrify
- Check Point Software Technologies
- Cisco
- Cloudflare
- Cyxtera Technologies
- Forcepoint
- Fortinet
- IBM
Tariff Impact Analysis: Key Insights for 2025
Global tariff negotiations across 180+ countries are reshaping supply chains, costs, and competitiveness. This report reflects the latest developments as of April 2025 and incorporates forward-looking insights into the market outlook.The analysts continuously track trade developments worldwide, drawing insights from leading global economists and over 200 industry and policy institutions, including think tanks, trade organizations, and national economic advisory bodies. This intelligence is integrated into forecasting models to provide timely, data-driven analysis of emerging risks and opportunities.
What’s Included in This Edition:
- Tariff-adjusted market forecasts by region and segment
- Analysis of cost and supply chain implications by sourcing and trade exposure
- Strategic insights into geographic shifts
Buyers receive a free July 2025 update with:
- Finalized tariff impacts and new trade agreement effects
- Updated projections reflecting global sourcing and cost shifts
- Expanded country-specific coverage across the industry
Table of Contents
I. METHODOLOGYII. EXECUTIVE SUMMARY2. FOCUS ON SELECT PLAYERSIII. MARKET ANALYSISCANADAITALYREST OF EUROPEREST OF WORLDIV. COMPETITION
1. MARKET OVERVIEW
3. MARKET TRENDS & DRIVERS
4. GLOBAL MARKET PERSPECTIVE
UNITED STATES
JAPAN
CHINA
EUROPE
FRANCE
GERMANY
UNITED KINGDOM
ASIA-PACIFIC
Companies Mentioned (Partial List)
A selection of companies mentioned in this report includes, but is not limited to:
- Akamai
- Centrify
- Check Point Software Technologies
- Cisco
- Cloudflare
- Cyxtera Technologies
- Forcepoint
- Fortinet
- IBM
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 89 |
| Published | April 2025 |
| Forecast Period | 2024 - 2030 |
| Estimated Market Value ( USD | $ 56.5 Billion |
| Forecasted Market Value ( USD | $ 160.2 Billion |
| Compound Annual Growth Rate | 19.0% |
| Regions Covered | Global |