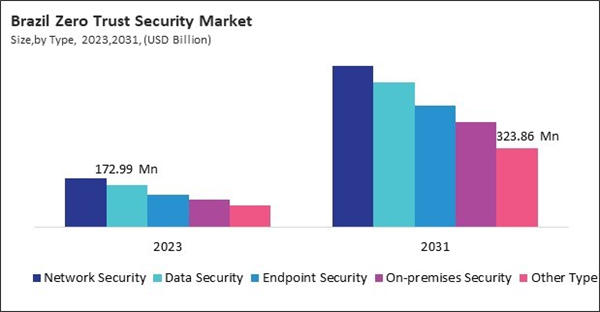
The Brazil market dominated the LAMEA Zero Trust Security Market by country in 2023, and is expected to continue to be a dominant market till 2031; thereby, achieving a market value of $2.50 billion by 2031. The Argentina market is showcasing a CAGR of 19% during 2024-2031. Additionally, the UAE market would register a CAGR of 17.2% during 2024-2031.
Companies rapidly shifted to cloud-based operations during the pandemic, which created a demand for zero trust security models to secure cloud environments and remote access. Enterprises and governments increased their cybersecurity budgets to address vulnerabilities exposed by the pandemic, resulting in greater adoption of zero trust architectures. The pandemic prompted stricter data protection regulations, compelling organizations to adopt zero trust security models to ensure compliance with remote workforce policies.
This market is experiencing rapid growth due to increasing cyber threats, data breaches, and the need for stringent security frameworks across industries. Organizations are shifting from traditional perimeter-based security to zero-trust architectures, emphasizing continuous verification, least privilege access, and micro-segmentation. Factors such as the rise of remote work, cloud adoption, and regulatory compliance requirements drive market expansion.
The market is witnessing significant growth as businesses and organizations increasingly prioritize robust cybersecurity frameworks. Two key factors driving the expansion of this market are Brazil’s booming e-commerce industry and the UAE’s expanding data center infrastructure. These developments intensify the demand for advanced cybersecurity solutions to protect sensitive data from evolving cyber threats. The UAE has emerged as a key data center hub in the Middle East, with increasing investments in cloud computing and digital infrastructure. The ITA reports that the UAE’s data center industry is expected to receive $1 billion in investments by 2026, growing at an annual rate of 3.43% from 2022 to 2027. This expansion is fuelled by the UAE’s drive toward smart cities, AI adoption, and cloud-based services. As data centers store and process vast amounts of sensitive information, they become prime targets for cyberattacks, necessitating the adoption of zero trust security architectures. With the surge in cloud-based services, Zero Trust Network Access (ZTNA) solutions are being deployed to secure workloads, preventing lateral movement of threats within data centers. The UAE government’s focus on cyber resilience and regulatory frameworks encourages enterprises to integrate these models to ensure data integrity and protection. In conclusion, Brazil’s fast-growing e-commerce sector and the UAE’s expanding data center industry present substantial opportunities for the market.
List of Key Companies Profiled
- Broadcom, Inc.
- Microsoft Corporation
- Fortinet, Inc.
- Palo Alto Networks, Inc.
- IBM Corporation
- Cisco Systems, Inc.
- Cloudflare, Inc.
- Check Point Software Technologies Ltd.
- CrowdStrike Holdings, Inc.
- Forcepoint LLC (Francisco Partners)
Market Report Segmentation
By Authentication
- Single-factor
- Multi-factor
By Deployment
- Cloud
- On-Premises
By Enterprise Size
- Large Enterprises
- SMEs
By Type
- Network Security
- Data Security
- Endpoint Security
- On-premises Security
- Other Type
By End Use
- BFSI
- IT & Telecom
- Retail
- Healthcare
- Other End Use
By Country
- Brazil
- Argentina
- UAE
- Saudi Arabia
- South Africa
- Nigeria
- Rest of LAMEA
Table of Contents
Companies Mentioned
- Broadcom, Inc.
- Microsoft Corporation
- Fortinet, Inc.
- Palo Alto Networks, Inc.
- IBM Corporation
- Cisco Systems, Inc.
- Cloudflare, Inc.
- Check Point Software Technologies Ltd.
- CrowdStrike Holdings, Inc.
- Forcepoint LLC (Francisco Partners)