CDR (Content Disarm and Reconstruction) is a computer security solution that removes potentially dangerous code from files. CDR technology, unlike malware analysis, does not determine or detect malicious capability, but instead excludes any file components which are not supported by the system's rules and policies. CDR is used to prevent cybersecurity threats from breaching the perimeter of a business network. Website traffic and email are two channels that CDR may be used to defend.
A phishing email is the source of the vast majority of malware infections. A considerable number of them employ a malicious document as the distribution mechanism. Over than 70% of phishing emails attachments or links and over 30% of fraudulent online downloads in 2020 were supplied via documents like PDF, Excel, Microsoft Office Word, and PowerPoint. Nevertheless, just because a document has been weaponized does not mean it is attempting to destroy.
Microsoft Office files are organised as ZIP files that contain folders holding a variety of different files. This indicates that the malicious script included within an Office file is merely one of numerous files contained within it. PDFs are similar in that they are likewise constructed from many elements. A malicious PDF file is made up of a number of components that work together to form the file which the receiver sees. Just one or a few such objects, however, contain the dangerous script code that is concealed within the page.
COVID-19 Impact Analysis
The COVID-19 pandemic has had a favourable influence on the market for content disarmament and reconstruction. CDR has acquired market traction in the midst of the continuing COVID-19 pandemic in order to cater to the escalating cyber-attacks and the growing use of remote working practises. The COVID-19 pandemic has posed a significant difficulty for businesses all over the world in maintaining operations despite the large closure of offices and other infrastructure. The increased usage of technologies, particularly in pandemic situations, to stay connected and run enterprises efficiently raises the risk of cyber-attacks.
As a result, the need for modern digital infrastructures has skyrocketed. These technologies have also grown in popularity and value as a target for hackers. During a pandemic, systems are more vulnerable to cyber-attacks. Enterprises are looking for ways to provide their staff with the resources and infrastructure they need to work remotely while maintaining company continuity.
Market Growth Factors:
Rising Costs Associated with Data Breaches
With the rise in file-sharing amongst coworkers working remotely and clients, partners, and suppliers – companies confront increased risks, threats, and exposures from file-borne malware, many of which are undetected by standard network security solutions. Malware assaults have serious repercussions. Companies incur data loss, service interruption, enterprise reputation harm, downtime, and revenue loss.
As a result, data breaches have a direct impact on the company's total market position. According to the Accenture Annual Cost of Cybersecurity research, the estimated average cost of a malware attack on a firm is USD 2.6 million, with these attacks losing the organisation an average of 50 days in lost time.
Increasing Demand for Cybersecurity Networks
The cybersecurity mesh is a modern structured methodology to security structures. It enables dispersed enterprises to supply and improve security where it is most needed. It's a decentralised concept that attempts to safeguard the identities of people or machines, and it's one of the trendiest strategies right now. The purpose, whether in cloud or on-premises, is to limit access to a company's network to authorised users (or systems). In principle, the cybersecurity mesh assists IT workers in maintaining security out of each access point even while blocking hackers from gaining access to the devices.
Marketing Restraining Factor:
Inadequate necessary skills and strategic management
The shortage of expertise among security specialists is a key issue that affects all big security firms. According to the conclusions of ISACA's State of Cybersecurity 2021 Part 1 survey study, the cyber security sector continues to face hiring and retention issues. India has a 9 percent greater deficit of cyber security workers than the worldwide norm. To resist cyberattacks, security professionals must have up-to-date knowledge and sophisticated abilities in forensic investigations, analytics, and cloud computing security.
The growing number of cyber security risks and file-based assaults has resulted in a scarcity of suitable IT security skills and personnel. Companies should take a proactive approach to deploying IT security infrastructure and training employees to forecast attacks by regularly monitoring data and conducting investigations. Preplanning assists businesses in picking the best CDR solution with all of the necessary capabilities and technology. As a result, a lack of competence and preparation is a stumbling block in the content disarms and rebuilding market.
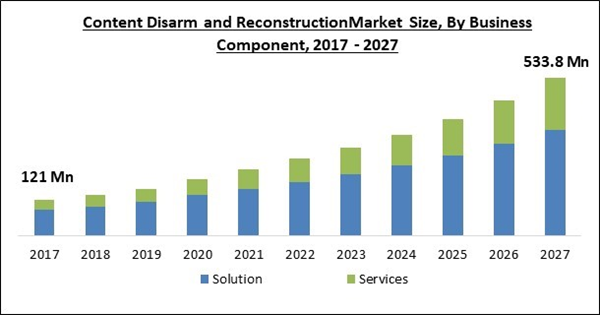
Component Outlook
Based on Component, the market is segmented into Solution and Services. The segment of Content Disarm and Reconstruction Solutions is predicted to provide the most market share. The content disarm and reconstruction technique ensures that the file's content is preserved while the potentially dangerous threat is eliminated. It eliminates the need to remove the file altogether, saving time and costs. Rising regulatory and compliance pressures, as well as an increase in cyber-attacks via different channels like attachments, USB transfers, emails, and file transfer protocol (FTP) transfers, have prompted the solution segment to generate greater revenue during the projection period.
Deployment Mode Outlook
Based on Deployment Mode, the market is segmented into On-premise and Cloud. During the projected period, the cloud deployment option is predicted to increase at a fast growth rate. CDR solutions are shifting to the cloud from on-premises deployment models because the former provides benefits such as lower operational costs and enabling technology available to companies and departments who lack funding and strong equipment to enable the on-premises deployment model. ECDR software can be put in the cloud, allowing numerous users to access information via the internet. Cloud services have no upfront costs and are paid for on an as-needed basis.
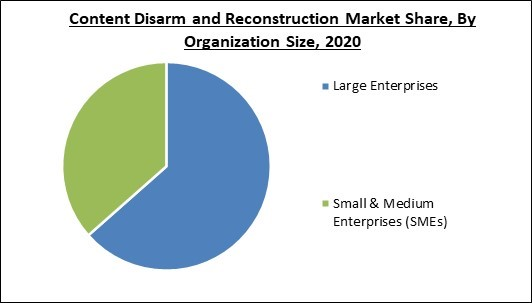
Organization Size Outlook
Based on Organization Size, the market is segmented into Large Enterprises and Small & Medium Enterprises (SMEs). By 2026, the large businesses segment is predicted to have a larger market share. The increasing digitization of numerous industrial verticals is increasing the susceptibility of businesses to cyber-attacks. Furthermore, the sophistication and complexity of cyber-attacks are increasing. In general, the majority of large-scale cyber-attacks targeted large organisations, and cyber thieves exploited user executions and detect phishing file attachments to attack these enterprises' networks. The frequency of zero-day cyberattacks is also rapidly increasing, and cyber criminals are exploiting the bulk of organisations' less competent security technologies and devices.
Vertical Outlook
Based on Vertical, the market is segmented into Government & Defense, BFSI, IT & Telecom, Manufacturing, Healthcare, Energy & Utilities and Others. The government and defence sector dominated the market, accounting for the lion's share. Cyberattacks are anticipated to attack personal data about the country's residents as well as military tactics. Untrustworthy hackers are constantly on the hunt for such information. The massive volumes of data processed and stored on-premises and in the cloud necessitate the development and deployment of secure systems capable of repelling any potential hacking attempts.
Regional Outlook
Based on Regions, the market is segmented into North America, Europe, Asia Pacific, and Latin America, Middle East & Africa. During the predicted period, APAC will increase at a faster CAGR. China, Australia, Japan, and the rest of Asia Pacific are examples of developing economies in the Asia Pacific area. It is very concerned about the rise in security costs as a result of the ever-changing danger situation. There are some well-established SMEs in the region. To meet the demands of their enormous client base, SMEs in this region are expanding at an exponential rate. In this region, innovative approaches such as IoT, machine learning, AI, and big data analytics are being used. Organizations are shifting their operations to the cloud in order to improve productivity and business success. The definition of cyber-attacks is always evolving and growing more complex.
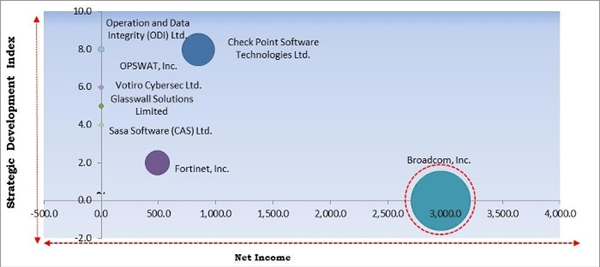
Cardinal Matrix - Content Disarm and Reconstruction Market Competition Analysis
The major strategies followed by the market participants are Product Launches and Partnerships. Based on the Analysis presented in the Cardinal matrix; Broadcom, Inc. is the major forerunner in the Content Disarm and Reconstruction Market. Companies such as Fortinet, Inc., Sasa Software (CAS) Ltd. and Glasswall Solutions Limited are some of the key innovators in the Market.
The market research report covers the analysis of key stake holders of the market. Key companies profiled in the report include Fortinet, Inc., Broadcom, Inc. (Symentec Corporation), Check Point Software Technologies Ltd., OPSWAT, Inc., Peraton, Inc. (Veritas Capital Fund Management, L.L.C.), Deep-Secure Ltd. (Forcepoint LLC.), Votiro Cybersec Ltd., Operation and Data Integrity (ODI) Ltd., Glasswall Solutions Limited, and Sasa Software (CAS) Ltd.
Recent Strategy Deployed in Content Disarm and Reconstruction Market
- Feb-2022: Check Point Software Technologies took over Spectral, an Israeli startup, and innovator in developer-first security tools designed by developers for developers. Through this acquisition, Check Point will extend its cloud solution, Check Point CloudGuard along with a developer-first security platform. In addition, this acquisition is expected to offer a vast range of cloud application security use cases including Infrastructure as Code (IaC) scanning and hardcoded secrets detection.
- Dec-2021: Odix formed a partnership with Integrity Labs to provide Integrity Labs clients with odix’s best-in-class anti-malware, and file disarmament tools to add to the cyber security toolbox. Together, the companies bring deep information security expertise and a “Prevent First” approach with a patented anti-malware technology that disarms malicious code from a file.
- Sep-2021: OPSWAT completed the acquisition of SNDBOX, the top malware analysis sandbox solution for critical infrastructure organizations. Under this acquisition, SNDBOX’s dynamic analysis technology is expected to combine with and empower OPSWAT’s MetaDefender platform and Malware Analysis Solution to enable organizations for securing their IT and OT environments, and utilize their security practices by automating malware analysis, enriching other intelligence systems, and bringing greater confidence to security and operational teams.
- Aug-2021: Check Point Software Technologies acquired Avanan, the fastest-growing cloud email security company. Under this acquisition, Avanan is expected to combine into the Check Point Infinity consolidated architecture for delivering the world’s most secure email security offering.
- Aug-2021: Fortinet partnered with Dragos, cybersecurity software. Under this partnership, Fortinet’s FortiGate is expected to combine into the Dragos Platform, focused on extending the benefits of the Security Fabric platform and leveraging its purpose-built Secure Processing Units (SPUs). Through this incorporation, customers is expected to be offered an integrated and robust security solution delivering asset visibility, inventory, vulnerability management, and threat detection for industrial asset owners.
- Aug-2021: Votiro introduced the addition of Google Chrome and Microsoft Edge browser solution to its Secure File Gateway solution for launching a new product. The product is expected to empower customer employees to safely download files from the web while removing all threats, both known and unknown, from downloaded files without any delays to worker productivity or business operations.
- Jul-2021: OPSWAT took over all assets of Bayshore Networks, the leading provider of active industrial cybersecurity protection solutions. Through this acquisition, key capabilities is expected to be added in unidirectional/bidirectional secure data transfer in critical networks, intrusion prevention for industrial devices, secure remote access for OT assets. In addition, the acquisition is expected to help in the expansion of OPSWAT’s mission to deliver best-in-class cybersecurity solutions to protect critical infrastructure.
- Feb-2021: Votiro launched a cloud-based SaaS version of its Secure File Gateway solutions. The new SaaS solution is expected to offer customers working within or migrating to the cloud a scalable way to completely eliminate file-borne attacks carried through email, web downloads, and website uploads. In addition, Votiro can also assist and host all infrastructures for enterprises, removing the need for organizations to stand up their own infrastructure or schedule updates.
- Sep-2020: Odix rolled out FileWall focused on small and medium-sized businesses (SMBs). This product is a native CDR-based security application for Microsoft Office 365 mailboxes available on Microsoft AppSource. In addition, Firewalls offer effective malware-disarming capabilities against file-based attacks, leveraging cutting-edge technology previously available only for enterprises.
- May-2020: Glasswall Launched Rebuild API, a cloud-hosted service that allows organizations to safely and securely import files and documents. Rebuild API authenticates the file types, settles out structural issues, and removes high-risk Active Content by the policy. Through this Files can be regenerated in seconds along with complete analysis.
- Feb-2020: Glasswall signed a distribution agreement with channel partners namely Data Ally (Greece), NewChannel (Benelux), Future Time (Italy), and Co.Next (Central and South East Europe). The agreement focused on the expansion of its Premier Partner Programme and its Content Disarm & Reconstruction (CDR) Solutions to Cybersecurity Markets Across Europe.
- Feb-2020: Sasa Software came into a partnership with SentinelOne, a pioneer in delivering autonomous security for the endpoint, data center, and cloud environments. The partnership aimed at combining the SentinelOne NextGen AI engine into the Sasa Software GateScanner CDR technology. Through this integration, the SentinelOne Nexus Embedded SDK, Sasa Software GateScanner Content Disarm, and Reconstruction technology can use SentinelOne’s predictive models for classifying files as benign or malicious according to their characteristics, without using signatures or cloud lookup.
- Jan-2020: SaSa Software entered into a partnership with MedOne for providing Global Cloud Services. Through this partnership, the companies aimed to offer GateScanner Content Disarm and Reconstruction (CDR) solutions as a Service by using MedOne’s Next Generation cloud infrastructures for the highest level of performance, availability, and security.
- Sep-2018: ODI introduced the first CDR anti-malware solution for managed security service providers. ODI’s TrueCDR technology prevents malware infiltration of organizational networks by deleting all malicious code from a wide range of file types. In addition, ODI’S has also been successful for both known and unknown malware.
Scope of the Study
Market Segments Covered in the Report:
By Component
- Solution
- Services
By Deployment Mode
- On-premise
- Cloud
By Organization Size
- Large Enterprises
- Small & Medium Enterprises (SMEs)
By Vertical
- Government & Defense
- BFSI
- IT & Telecom
- Manufacturing
- Healthcare
- Energy & Utilities
- Others
By Geography
- North America
- US
- Canada
- Mexico
- Rest of North America
- Europe
- Germany
- UK
- France
- Russia
- Spain
- Italy
- Rest of Europe
- Asia Pacific
- China
- Japan
- India
- South Korea
- Singapore
- Malaysia
- Rest of Asia Pacific
- LAMEA
- Brazil
- Argentina
- UAE
- Saudi Arabia
- South Africa
- Nigeria
- Rest of LAMEA
Key Market Players
List of Companies Profiled in the Report:
- Fortinet, Inc.
- Broadcom, Inc. (Symentec Corporation)
- Check Point Software Technologies Ltd.
- OPSWAT, Inc.
- Peraton, Inc. (Veritas Capital Fund Management, L.L.C.)
- Deep-Secure Ltd. (Forcepoint LLC.)
- Votiro Cybersec Ltd.
- Operation and Data Integrity (ODI) Ltd.
- Glasswall Solutions Limited
- Sasa Software (CAS) Ltd.
Unique Offerings from the Publisher
- Exhaustive coverage
- The highest number of market tables and figures
- Subscription-based model available
- Guaranteed best price
- Assured post sales research support with 10% customization free
Table of Contents
Companies Mentioned
- Fortinet, Inc.
- Broadcom, Inc. (Symentec Corporation)
- Check Point Software Technologies Ltd.
- OPSWAT, Inc.
- Peraton, Inc. (Veritas Capital Fund Management, L.L.C.)
- Deep-Secure Ltd. (Forcepoint LLC.)
- Votiro Cybersec Ltd.
- Operation and Data Integrity (ODI) Ltd.
- Glasswall Solutions Limited
- Sasa Software (CAS) Ltd.