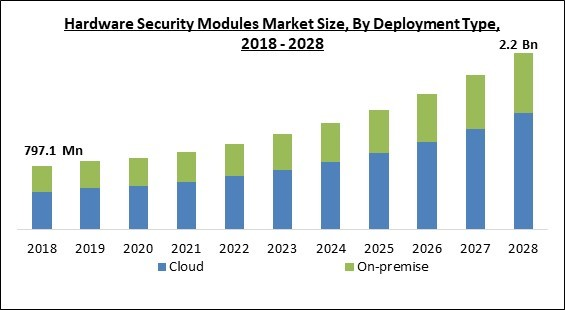
The Global Hardware Security Modules Market size is expected to reach $2.2 billion by 2028, rising at a market growth of 12.8% CAGR during the forecast period.
A hardware security module is a physical computing device that safeguards and manages digital keys and conducts digital signature decryption and encryption rapid verification, along with other cryptographic operations. Typically, these modules exist as plug-in cards or external units that are directly connected to a network or computer server.
To maintain customer confidence in the digital realm, organizations primarily need hardware security components. They ensure comprehensive protection against cyber-attacks. The astronomical demand for hardware security modules was initiated by financial institutions and banks in order to protect the payment process via debit and credit cards issued by big corporations, such as Mastercard and Visa.
Hardware security modules encrypt and decode data for authentication, digital signatures, and other cryptographic processes. They are specifically designed to protect cryptographic keys for an extended length of time. Hardware security modules can create a safe environment for the execution of cryptographic operations, like a key exchange, key management, and encryption. A hardware security module is a physical device that provides additional protection for sensitive data.
This type of hardware is primarily used for the use of apps, databases, and identities. Businesses can use hardware security modules to safeguard valuable trade secrets by ensuring that only authorized users can access the hardware security modules component to conduct a cryptographic key transaction.
The leading players in the market are competing with diverse innovative offerings to remain competitive in the market. The below illustration shows the percentage of revenue shared by some of the leading companies in the market. The leading players of the market are adopting various strategies in order to cater demand coming from the different industries. The key developmental strategies in the market are Acquisitions, and Partnerships & Collaborations.
The market research report covers the analysis of key stake holders of the market. Key companies profiled in the report include Microsoft Corporation, Amazon.com, Inc., IBM Corporation, Microchip Technology, Inc., Thales Group S.A., Atos Group, Futurex LP, STMicroelectronics N.V., Lattice Semiconductor Corporation and Infineon Technologies AG
A hardware security module is a physical computing device that safeguards and manages digital keys and conducts digital signature decryption and encryption rapid verification, along with other cryptographic operations. Typically, these modules exist as plug-in cards or external units that are directly connected to a network or computer server.
To maintain customer confidence in the digital realm, organizations primarily need hardware security components. They ensure comprehensive protection against cyber-attacks. The astronomical demand for hardware security modules was initiated by financial institutions and banks in order to protect the payment process via debit and credit cards issued by big corporations, such as Mastercard and Visa.
Hardware security modules encrypt and decode data for authentication, digital signatures, and other cryptographic processes. They are specifically designed to protect cryptographic keys for an extended length of time. Hardware security modules can create a safe environment for the execution of cryptographic operations, like a key exchange, key management, and encryption. A hardware security module is a physical device that provides additional protection for sensitive data.
This type of hardware is primarily used for the use of apps, databases, and identities. Businesses can use hardware security modules to safeguard valuable trade secrets by ensuring that only authorized users can access the hardware security modules component to conduct a cryptographic key transaction.
COVID-19 Impact Analysis
The coronavirus pandemic has significantly impacted the market for hardware security modules. The suspension of new construction projects all over the world has decreased the demand for analog semiconductors. As a result of the government's implementation of stringent rules, which disrupted supply chains, manufacturers throughout the world have failed to incorporate new hardware security modules because workers have stayed at home due to lockdowns that were imposed by the government in order to regulate the diffusion of the infection. The virus had a significant effect on the market since production and the supply chain were halted.Market Growth Factors
An Increase in The Number of Cyber-Attacks and Data Breaches All Over the World
A data breach is an occurrence in which information is stolen or removed from a system without the owner's consent or knowledge. Typically, large businesses and organizations are the targets of data breaches. The stolen information may be sensitive, proprietary, or private, such as customer data, credit card numbers, trade secrets, and national security information. Government and healthcare companies are the top targets of cyberattacks, despite enhanced protection, due to the valuable personal data they gather, which may be sold.Rising and Rapid Penetration Of 5G
5G offers an abundance of growth potential for enterprises. However, if security concerns are not addressed with a modern trust model for the era of 5G, these benefits might pose threats and risks to the integrity and confidentiality of vital data. Multiple data types can be handled everywhere with 5G, from the network's edge to its core. Due to 5G, the security environment is developing. Beyond consumer mobile broadband, there is a growing requirement for security to successfully meet an expanding number of new user devices and cases across companies and organizations. For 5G to be secure, sensitive data must be protected.Marketing Restraining Factor
Requirement for Frequent Maintenance and Upgrades
Hardware security is just as crucial for day-to-day company operations as software security. However, hardware security is often overlooked. One of the major factors that pose challenges in the deployment of HSM is the high cost of the upgrades that are required to protect the system and user privacy. Because hardware security module upgrades are costly, vulnerabilities exist. Businesses must continuously upgrade their cybersecurity systems in order to accommodate emerging technology.The leading players in the market are competing with diverse innovative offerings to remain competitive in the market. The below illustration shows the percentage of revenue shared by some of the leading companies in the market. The leading players of the market are adopting various strategies in order to cater demand coming from the different industries. The key developmental strategies in the market are Acquisitions, and Partnerships & Collaborations.
Deployment Type Outlook
Based on Deployment Type, the Hardware Security Modules Market is bifurcated into On-premise and Cloud. In 2021, the on-premise segment garnered a significant revenue share of the hardware security modules market. The rapid increase in the growth of the segment is majorly attributed to the higher security of the on-premise setting of this solution. When the solution is deployed within company-owned systems, it allows the company to protect the privacy of the solution from cyber-attacks that are more probable over public clouds.Application Outlook
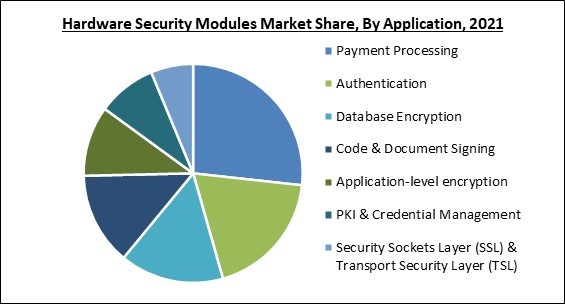
By Application, the Hardware Security Modules Market is categorized into Payment Processing, Code and Document Signing, Authentication, Application-level encryption, Database Encryption, PKI and Credential Management, and Security Sockets Layer (SSL) and Transport Security Layer (TSL). In 2021, the payment processing segment witnessed the biggest revenue share of the hardware security module market. Payment processing refers to the services and procedures that automate merchant-customer payment interactions. A computer or system processes, validates, and accepts or denies transactions using a secure Internet connection on behalf of the business.Type Outlook
On the basis of Type, the Hardware Security Modules Market is segregated into LAN Based/ Network Attached, PCI-Based/ Embedded Plugins, USB Based/ Portable, and Smart Cards. In 2021, the USB-based/portable segment garnered a significant revenue share of the hardware security module market. USB-based/portable hardware security modules with a compact form factor are used for digital code, signature, document signing, and secure key storage. These modules are appropriate for offline circumstances where the module must be placed in a physical safe while not in use or where portability is required.Vertical Outlook
Based on Vertical, the Hardware Security Modules Market is segmented into Consumer Goods & Retail, BFSI, Aerospace & defense, Public Sector/ Government, Energy and Power, Industrial Manufacturing, Medical and Life Sciences, Transportation, and IT & Telecommunications. In 2021, the Medical and Life Sciences segment garnered a promising revenue share of the hardware security module market. The rapid surge in the growth of the segment is attributed to the increasing efforts of hospitals as well as clinics in order to offer an enhanced and secure experience to their patients.Regional Outlook
Region-Wise, the Hardware Security Modules Market is analyzed across North America, Europe, Asia-Pacific, and LAMEA. In 2021, Europe held the largest revenue in the hardware security module market. The increase in the growth of the market is estimated to be propelled by the highly competitive landscape of the regional market. The considerable presence of key firms delivering cloud-based services across the hardware security modules market in Europe for various verticals, such as healthcare and IT & telecom, also contributes to the growth of the market in this region.The market research report covers the analysis of key stake holders of the market. Key companies profiled in the report include Microsoft Corporation, Amazon.com, Inc., IBM Corporation, Microchip Technology, Inc., Thales Group S.A., Atos Group, Futurex LP, STMicroelectronics N.V., Lattice Semiconductor Corporation and Infineon Technologies AG
Strategies Deployed in Hardware Security Modules Market
- Nov-2021: STMicroelectronics rolled out the ST31N600, a range of secure microcontroller for dCVV and biometric system-on-card solutions. Through this product launch, the company aimed to integrate circuitry for energy harvesting as well as additional connectivity in order to allow battery-free smartcards to offer improved user authentication in online and contactless transactions.
- Oct-2021: STMicroelectronics teamed up with Sierra Wireless, a leader in providing IoT services. Under this collaboration, the companies aimed to enable the STM32 MCU user community to optimize the utilization of Sierra's flexible cellular IoT connectivity as well as edge-to-cloud solutions.
- Oct-2021: Infineon Technologies unveiled the SLS37 V2X HSM, a plug-and-play security solution. The new product aimed to eliminate the burden of Security Certification from the host processor that operates Linux operating system through its tamper resistant and highly secured microcontroller.
- Dec-2020: IBM acquired Instana, a leader in application performance monitoring and enterprise observability. Through this acquisition, the company aimed to provide best-in-class AI-built automation capabilities in order to streamline the complexities of modern applications, including hybrid cloud landscapes. Furthermore, the acquisition of Instana would allow IBM’s ITOps and DevOps to contextualize and accumulate multiple performance data sources.
- Oct-2020: Microchip Technology rolled out the WFI32E01PC, the first-ever Wi-Fi microcontroller of the company. The new solution aimed to offer verifiable, hardcoded, and reliable identity to devices in order to connect to the cloud securely.
- Jun-2020: IBM took over Spanugo, a cloud cybersecurity posture management solutions provider. Through this acquisition, the company aimed to fulfill the rising customer demand for increased security within highly regulated industries through the integration of Spanugo's technology into its financial services public cloud.
- Jun-2020: Futurex introduced enhancements in its VirtuCrypt financial cloud HSM. With this product expansion, the company aimed to leverage its cloud HSM expertise in order to complement its strategy to comply with the robustness, scalability, security, and compliance requirements of financial services organizations throughout the world.
- Apr-2019: Thales completed its acquisition of Gemalto, a digital security company. Following this acquisition, the company aimed to address challenges, like data and network cyber security, unmanned air traffic management, and airport security and financial transaction security through the integration of the technologies and expertise of Gemalto.
- Oct-2018: Atos launched the Horus range of trust infrastructures appliances, a line of pre-configured software appliances. Through this launch, the company aimed to facilitate the deployment of deployment of trust services on the basis of digital identities. Furthermore, the new range of solutions include electronic signatures, Public Key Infrastructure, user explicit consent for qualified signature, timestamping, and blockchain services.
Scope of the Study
By Deployment Type
- Cloud
- On-premise
By Application
- Payment Processing
- Authentication
- Database Encryption
- Code & Document Signing
- Application-level encryption
- PKI & Credential Management
- Security Sockets Layer (SSL) & Transport Security Layer (TSL)
By Type
- LAN Based/ Network Attached
- PCI-Based/ Embedded Plugins
- USB Based/ Portable & Smart Cards
By Vertical
- BFSI
- Public Sector/ Government
- Aerospace & Defense
- Medical & Life Sciences
By Geography
- North America
- US
- Canada
- Mexico
- Rest of North America
- Europe
- Germany
- UK
- France
- Russia
- Spain
- Italy
- Rest of Europe
- Asia Pacific
- China
- Japan
- India
- South Korea
- Singapore
- Malaysia
- Rest of Asia Pacific
- LAMEA
- Brazil
- Argentina
- UAE
- Saudi Arabia
- South Africa
- Nigeria
- Rest of LAMEA<
Key Market Players
List of Companies Profiled in the Report:
- Microsoft Corporation
- com, Inc.
- IBM Corporation
- Microchip Technology, Inc.
- Thales Group S.A.
- Atos Group
- Futurex LP
- STMicroelectronics N.V.
- Lattice Semiconductor Corporation
- Infineon Technologies AG
Unique Offerings
- Exhaustive coverage
- The highest number of market tables and figures
- Subscription-based model available
- Guaranteed best price
- Assured post sales research support with 10% customization free
Table of Contents
Chapter 1. Market Scope & Methodology
Chapter 2. Market Overview
Chapter 3. Competition Analysis - Global
Chapter 4. Global Hardware Security Modules Market by Deployment Type
Chapter 5. Global Hardware Security Modules Market by Application
Chapter 6. Global Hardware Security Modules Market by Type
Chapter 7. Global Hardware Security Modules Market by Vertical
Chapter 8. Global Hardware Security Modules Market by Region
Chapter 9. Company Profiles
Companies Mentioned
- Microsoft Corporation
- Amazon.com, Inc.
- IBM Corporation
- Microchip Technology, Inc.
- Thales Group S.A.
- Atos Group
- Futurex LP
- STMicroelectronics N.V.
- Lattice Semiconductor Corporation
- Infineon Technologies AG
Methodology

LOADING...
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 343 |
| Published | October 2022 |
| Forecast Period | 2021 - 2028 |
| Estimated Market Value ( USD | $ 981 Million |
| Forecasted Market Value ( USD | $ 2231 Million |
| Compound Annual Growth Rate | 12.8% |
| Regions Covered | Global |
| No. of Companies Mentioned | 10 |