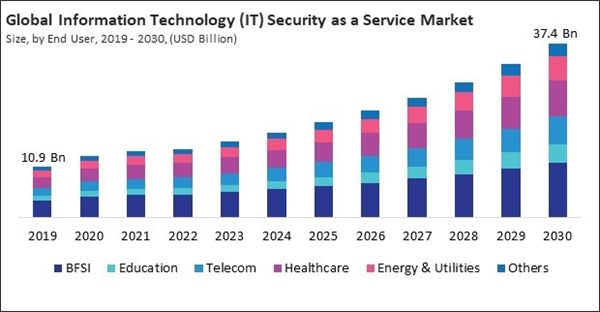
The telecom segment is witnessing continuous network expansion, including deploying 5G technology. Therefore, the telecom segment captured $2255.7 million revenue in the market in 2022. The demand for IT security services rises as telecom operators and service providers seek solutions to secure their expansive networks, protect critical infrastructure, and ensure the integrity of communication channels.
The major strategies followed by the market participants are Mergers & Acquisition as the key developmental strategy to keep pace with the changing demands of end users. For instance, In September, 2023, Cisco Systems Inc. completed the acquisition of Splunk Inc., an American software company. Through this acquisition, the companies helped to make organizations more secure and resilient. Additionally, In April, 2023, Trend Micro Inc. acquired Anlyz Cybersecure Private Limited to incorporate its functionalities into Trend Micro's unified cybersecurity platform, Vision One.
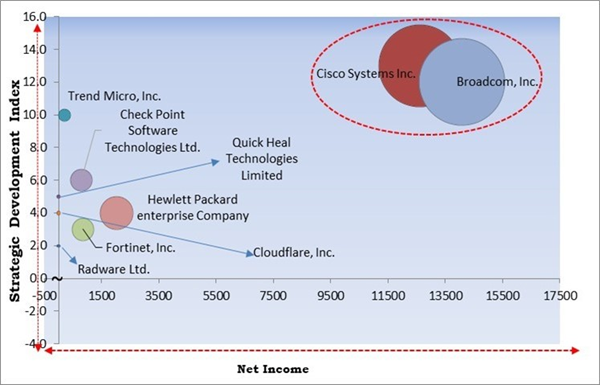
Cardinal Matrix - Market Competition Analysis
Based on the Analysis presented in the Cardinal Matrix; Cisco Systems Inc. and Broadcom, Inc. are the forerunners in the market. In November, 2023, Broadcom Inc. completed the acquisition of VMware, Inc., an American cloud computing and virtualization technology company. Through this acquisition, the Broadcom Software portfolio was combined with the VMware platform to provide critical infrastructure solutions to customers. Companies such as Hewlett Packard enterprise Company, Check Point Software Technologies Ltd., Fortinet, Inc. are some of the key innovators in the market.Market Growth Factors
Customizable solutions allow organizations to define and implement security postures based on their unique requirements, industry regulations, and risk profiles. IT security as a service provider provides customizable security solutions that may be tailored to the specific needs of various industries and organizations. This ensures that security measures align with the organization's objectives and compliance requirements. Thus, because of the increasing customizable and scalable solutions, the market is anticipated to increase significantly.Additionally, SMEs often experience dynamic growth, and their cybersecurity needs evolve accordingly. IT security as a service provider offers scalable solutions that can grow with the business. SMEs can adjust their subscription plans and security services as their operations expand, ensuring that cybersecurity measures remain effective and aligned with business growth. Hence, small, and medium-sized enterprises (SMEs) adoption have been a pivotal factor in driving the growth of the market.
Market Restraining Factors
IT security as a service provider often relies on third-party vendors for components, software, and infrastructure. Vulnerabilities in the products or services supplied by third parties can be exploited by malicious actors, compromising the overall security of IT security services. The chain is only as strong as its weakest link. Limited visibility into the entire supply chain can make it challenging for IT security as a service provider to assess and mitigate risks effectively. Thus, lack of supply chain challenges can slow down the growth of the market.By Offering Analysis
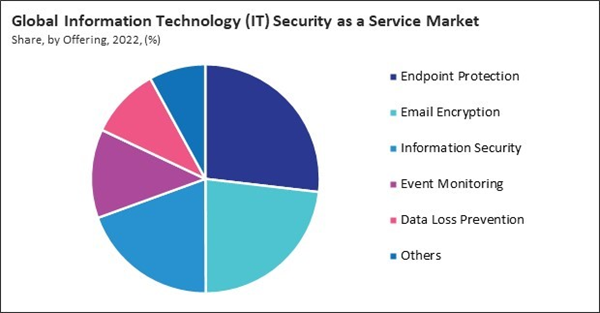
By offering, the market is categorized into email encryption, endpoint protection, data loss prevention, event monitoring, information security, and others. The email encryption segment covered 23.1% revenue share in the market in 2022. Email encryption protects the confidentiality of sensitive information transmitted by email by transforming it into an indistinct format that can only be deciphered by authorized receivers.By End User Analysis
Based on end user, the market is classified into BFSI, healthcare, telecom, energy & utilities, education, and others. The healthcare segment acquired 21.3% revenue share in the market in 2022. IT security services protect patient data, including electronic health records (EHRs), medical histories, and other sensitive information, safeguarding it from unauthorized access, breaches, or misuse.By Regional Analysis
Region-wise, the market is analysed across North America, Europe, Asia Pacific, and LAMEA. In 2022, the North America region led the market by generating 34.1% revenue share. North America faces a continuous and evolving landscape of cybersecurity threats, including ransomware, phishing, and advanced persistent threats (APTs).Recent Strategies Deployed in the Market
- Nov-2023: Broadcom Inc. completed the acquisition of VMware, Inc., an American cloud computing and virtualization technology company. Through this acquisition, the Broadcom Software portfolio was combined with the VMware platform to provide critical infrastructure solutions to customers.
- Oct-2023: Quick Heal Technologies Limited unveiled the metaProtect. The new product is a cloud-based platform for remote security and privacy management. The new product assists in safeguarding the devices of the entire family.
- Sep-2023: Cisco Systems Inc. completed the acquisition of Splunk Inc., an American software company. Through this acquisition, the companies helped to make organizations more secure and resilient.
- Aug-2023: Check Point Software Technologies Ltd. completed the acquisition of Perimeter 81 Ltd., an Israeli cloud and network security company. Through this acquisition, Check Point integrated the capabilities of Perimeter 81 into the architecture of Check Point Infinity. Additionally, the acquisition helped Check Point by offering secure access to remote users and providing SSE solutions in the market.
- Aug-2023: Radware Ltd. entered into an agreement with Spark New Zealand Limited, a New Zealand telecommunications and digital services company. Under this agreement, the companies offered applications and network security services to their customers in New Zealand. Additionally, the agreement helped Spark in the distribution of the applications and the network security solutions to the customers in New Zealand.
List of Key Companies Profiled
- Quick Heal Technologies Limited
- Trend Micro, Inc.
- Radware Ltd.
- Cisco Systems Inc.
- Broadcom, Inc.
- Cloudflare, Inc.
- Check Point Software Technologies Ltd.
- Hewlett Packard enterprise Company
- Barracuda Networks, Inc. (KKR & Co. Inc.)
- Fortinet, Inc.
Market Report Segmentation
By End User- BFSI
- Education
- Telecom
- Healthcare
- Energy & Utilities
- Others
- Endpoint Protection
- Email Encryption
- Information Security
- Event Monitoring
- Data Loss Prevention
- Others
- North America
- US
- Canada
- Mexico
- Rest of North America
- Europe
- Germany
- UK
- France
- Russia
- Spain
- Italy
- Rest of Europe
- Asia Pacific
- China
- Japan
- India
- South Korea
- Singapore
- Malaysia
- Rest of Asia Pacific
- LAMEA
- Brazil
- Argentina
- UAE
- Saudi Arabia
- South Africa
- Nigeria
- Rest of LAMEA
Table of Contents
Companies Mentioned
- Quick Heal Technologies Limited
- Trend Micro, Inc.
- Radware Ltd.
- Cisco Systems Inc.
- Broadcom, Inc.
- Cloudflare, Inc.
- Check Point Software Technologies Ltd.
- Hewlett Packard enterprise Company
- Barracuda Networks, Inc. (KKR & Co. Inc.)
- Fortinet, Inc.