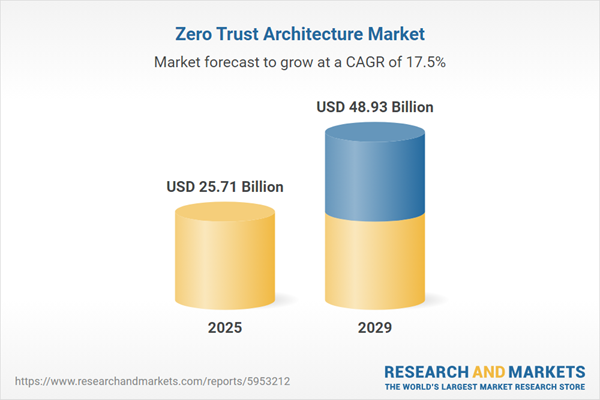
The zero trust architecture market size has grown rapidly in recent years. It will grow from $21.84 billion in 2024 to $25.71 billion in 2025 at a compound annual growth rate (CAGR) of 17.7%. The growth in the historic period can be attributed to data breaches and cyber attacks, digital transformation, remote access requirements, zero trust frameworks and standards, regulatory compliance requirements.
The zero trust architecture market size is expected to see rapid growth in the next few years. It will grow to $48.93 billion in 2029 at a compound annual growth rate (CAGR) of 17.5%. The growth in the forecast period can be attributed to cloud adoption and migration, vendor and supply chain risk management, security threat landscape, internal and external threat intelligence, incident response preparedness. Major trends in the forecast period include zero trust as a service (ZTAAS), zero trust for devsecops, zero trust for remote workforce, convergence with identity-centric security, zero trust analytics and behavioral monitoring.
Increasing cyber security threats are expected to propel the growth of the zero-trust architecture market going forward. Cyber security refers to the practice of protecting computer systems, networks, devices, and data from unauthorized access, cyber-attacks, theft, damage, or other malicious activities. Zero-trust architecture enhances cybersecurity resilience by adopting a proactive and comprehensive approach to identity verification, access control, and risk management, effectively mitigating cyber threats and protecting critical assets and data from unauthorized access and exploitation. For instance, in January 2023, according to the Australian Cyber Security Centre, an Australia-based cyber security operations center, 38% increase in global cyber-attacks in 2022, compared to 2021. In 2022, 83% of the organizations experienced multiple data breaches and 60% of data breaches resulted in price increases that were passed on to customers. Therefore, increasing cyber security threats are driving the zero-trust architecture market.
Major companies operating in the zero-trust architecture market are focused on developing innovative products with advanced technological solutions such as the updated version of zerpo trust security to increase demand in the market. It helps companies create implementation plans and zero-trust strategies. It is predicated on the principles of zero trust and offers particular instances of initial, progressive, ideal, and conventional zero trust architectures. For instance, in April 2023, Cyber security and Infrastructure Security Agency, a US-based government agency, released an updated Zero Trust Maturity Model Version 2. The model seeks to offer the transparency required to aid in the creation, application, upholding, and modification of security policies. For companies aiming to shift to a zero-trust architecture, it is an invaluable tool that provides direction and illustrations to evaluate their progress and schedule the necessary expenditures to move closer to a zero-trust setting.
In September 2023, Check Point Software Technologies Ltd., a US-based provider of cyber security solutions, acquired Perimeter 81 Ltd. for approximately $490 million. The acquisition is aimed at strengthening Check Point's position in the secure access service edge (SASE) market and ensuring fast and secure access to remote sites, data centers, and the internet. Perimeter 81 Ltd. is an Israeli-based cloud and network security company, delivers a converged network and security platform that connects users to corporate resources, and its technology offers capabilities such as zero trust access and full mesh connectivity.
Major companies operating in the zero trust architecture market are Google LLC, Microsoft Corporation, International Business Machines Corporation, Cisco Systems Inc, Broadcom Inc, VMware Inc, Palo Alto Networks Inc, Fortinet Inc, Akamai Technologies Inc, Citrix Systems Inc., Check Point Software Technologies Ltd, Trellix, Proofpoint Inc, CrowdStrike Holdings Inc, Netskope Inc, Okta Inc, Zscaler Inc, Cloudflare Inc, Cyxtera Technologies Inc, Forcepoint LLC, Ivanti, Nord Security, Musarubra US LLC (Skyhigh Security), Versa Networks Inc, Perimeter 81 Ltd, Appgate Inc, Axis Cyber Security Ltd, Twingate Inc, Zero Networks, GoodAccess, Cloud Software Group Inc.
North America was the largest region in the zero trust architecture market in 2024. Asia-Pacific is expected to be the fastest-growing region in the forecast period. The regions covered in the zero trust architecture market report are Asia-Pacific, Western Europe, Eastern Europe, North America, South America, Middle East, Africa. The countries covered in the zero trust architecture market report are Australia, Brazil, China, France, Germany, India, Indonesia, Japan, Russia, South Korea, UK, USA, Canada, Italy, Spain.
The zero trust architecture market consists of revenues earned by entities by providing services such as network security services, cloud security services, endpoint security services, data security services and user and device management services. The market value includes the value of related goods sold by the service provider or included within the service offering. The zero trust architecture market also includes sales of identity and authentication devices, network access control (nac) devices, endpoint management devices, and encryption devices. Values in this market are ‘factory gate’ values, that is the value of goods sold by the manufacturers or creators of the goods, whether to other entities (including downstream manufacturers, wholesalers, distributors and retailers) or directly to end customers. The value of goods in this market includes related services sold by the creators of the goods.
The market value is defined as the revenues that enterprises gain from the sale of goods and/or services within the specified market and geography through sales, grants, or donations in terms of the currency (in USD, unless otherwise specified).
Zero trust architecture (ZTA) is a cybersecurity approach that assumes that no connection, user, or asset is trustworthy until verified. Its goal is to minimize attack surfaces and reduce exposure to cyberattacks by continuously verifying identities and access rights throughout the entire digital ecosystem.
The main offerings of the zero trust architecture are solutions and services. Solution refers to a homogeneous mixture of one or more solutes dissolved in a solvent. The size of organization includes small and medium-sized enterprises (SMEs), and large enterprises, with mode of deployment such as cloud and on-premises. It is used in network security, data security, endpoint security, cloud security, application security, and are used for banking, financial services, and insurance (BFSI), government and defense, information technology and information technology-enabled services, healthcare, retail and e-commerce, energy and utilities, and others.
The main offerings of the zero trust architecture are solutions and services. Solution refers to a homogeneous mixture of one or more solutes dissolved in a solvent. The size of organization includes small and medium-sized enterprises (SMEs), and large enterprises, with mode of deployment such as cloud and on-premises. It is used in network security, data security, endpoint security, cloud security, application security, and are used for banking, financial services, and insurance (BFSI), government and defense, information technology and information technology-enabled services, healthcare, retail and e-commerce, energy and utilities, and others.
The revenues for a specified geography are consumption values that are revenues generated by organizations in the specified geography within the market, irrespective of where they are produced. It does not include revenues from resales along the supply chain, either further along the supply chain or as part of other products.
This product will be delivered within 3-5 business days.
Table of Contents
Executive Summary
Zero Trust Architecture Global Market Report 2025 provides strategists, marketers and senior management with the critical information they need to assess the market.This report focuses on zero trust architecture market which is experiencing strong growth. The report gives a guide to the trends which will be shaping the market over the next ten years and beyond.
Reasons to Purchase:
- Gain a truly global perspective with the most comprehensive report available on this market covering 15 geographies.
- Assess the impact of key macro factors such as conflict, pandemic and recovery, inflation and interest rate environment and the 2nd Trump presidency.
- Create regional and country strategies on the basis of local data and analysis.
- Identify growth segments for investment.
- Outperform competitors using forecast data and the drivers and trends shaping the market.
- Understand customers based on the latest market shares.
- Benchmark performance against key competitors.
- Suitable for supporting your internal and external presentations with reliable high quality data and analysis
- Report will be updated with the latest data and delivered to you along with an Excel data sheet for easy data extraction and analysis.
- All data from the report will also be delivered in an excel dashboard format.
Description
Where is the largest and fastest growing market for zero trust architecture? How does the market relate to the overall economy, demography and other similar markets? What forces will shape the market going forward? The zero trust architecture market global report answers all these questions and many more.The report covers market characteristics, size and growth, segmentation, regional and country breakdowns, competitive landscape, market shares, trends and strategies for this market. It traces the market’s historic and forecast market growth by geography.
- The market characteristics section of the report defines and explains the market.
- The market size section gives the market size ($b) covering both the historic growth of the market, and forecasting its development.
- The forecasts are made after considering the major factors currently impacting the market. These include:
- The forecasts are made after considering the major factors currently impacting the market. These include the Russia-Ukraine war, rising inflation, higher interest rates, and the legacy of the COVID-19 pandemic.
- Market segmentations break down the market into sub markets.
- The regional and country breakdowns section gives an analysis of the market in each geography and the size of the market by geography and compares their historic and forecast growth. It covers the growth trajectory of COVID-19 for all regions, key developed countries and major emerging markets.
- The competitive landscape chapter gives a description of the competitive nature of the market, market shares, and a description of the leading companies. Key financial deals which have shaped the market in recent years are identified.
- The trends and strategies section analyses the shape of the market as it emerges from the crisis and suggests how companies can grow as the market recovers.
Scope
Markets Covered:
1) By Offering: Solution, Services2) By Organization Size: Small And Medium-Sized Enterprises (SMEs), Large Enterprises
3)By Deployment Mode: Cloud, On-Premises
4) By Application: Network Security, Data Security, Endpoint Security, Cloud Security, Application Security
5) By Vertical: Banking, Financial Services, And Insurance (BFSI), Government And Defense, Information Technology And Information Technology Enabled Services, Healthcare, Retail And Ecommerce, Energy And Utilities, Other Verticals
Subsegments:
1) By Solution: Identity And Access Management (IAM); Network Security Solutions; Data Security Solutions; Endpoint Security Solutions; Security Information And Event Management (SIEM); Threat Detection And Response Solutions2) By Services: Consulting Services; Integration And Implementation Services; Managed Security Services; Training And Support Services; Compliance And Risk Assessment Services
Key Companies Mentioned: Google LLC; Microsoft Corporation; International Business Machines Corporation; Cisco Systems Inc; Broadcom Inc
Countries: Australia; Brazil; China; France; Germany; India; Indonesia; Japan; Russia; South Korea; UK; USA; Canada; Italy; Spain
Regions: Asia-Pacific; Western Europe; Eastern Europe; North America; South America; Middle East; Africa
Time Series: Five years historic and ten years forecast.
Data: Ratios of market size and growth to related markets, GDP proportions, expenditure per capita.
Data Segmentation: Country and regional historic and forecast data, market share of competitors, market segments.
Sourcing and Referencing: Data and analysis throughout the report is sourced using end notes.
Delivery Format: PDF, Word and Excel Data Dashboard.
Companies Mentioned
Some of the major companies featured in this Zero Trust Architecture market report include:- Google LLC
- Microsoft Corporation
- International Business Machines Corporation
- Cisco Systems Inc
- Broadcom Inc
- VMware Inc
- Palo Alto Networks Inc
- Fortinet Inc
- Akamai Technologies Inc
- Citrix Systems Inc.
- Check Point Software Technologies Ltd
- Trellix
- Proofpoint Inc
- CrowdStrike Holdings Inc
- Netskope Inc
- Okta Inc
- Zscaler Inc
- Cloudflare Inc
- Cyxtera Technologies Inc
- Forcepoint LLC
- Ivanti
- Nord Security
- Musarubra US LLC (Skyhigh Security)
- Versa Networks Inc
- Perimeter 81 Ltd
- Appgate Inc
- Axis Cyber Security Ltd
- Twingate Inc
- Zero Networks
- GoodAccess
- Cloud Software Group Inc
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 200 |
| Published | March 2025 |
| Forecast Period | 2025 - 2029 |
| Estimated Market Value ( USD | $ 25.71 Billion |
| Forecasted Market Value ( USD | $ 48.93 Billion |
| Compound Annual Growth Rate | 17.5% |
| Regions Covered | Global |
| No. of Companies Mentioned | 32 |