Healthcare is the fastest growing segment, North America is the largest market globally
Speak directly to the analyst to clarify any post sales queries you may have.
10% Free customizationThis report comes with 10% free customization, enabling you to add data that meets your specific business needs.
Key Market Drivers
The escalating frequency and sophistication of cyberattacks represent a primary driver for the global application security market. As organizations increasingly rely on complex applications to conduct business, these applications become prime targets for malicious actors employing advanced tactics such as ransomware, supply chain attacks, and zero-day exploits. The sheer volume of these attacks necessitates robust application security measures to prevent data breaches, service disruptions, and financial lossesKey Market Challenges
The persistent global shortage of skilled cybersecurity professionals presents a considerable challenge to the growth of the Global Application Security Market. This deficit directly impedes the effective implementation and ongoing management of robust application security solutions. Organizations frequently encounter delays in deploying new security technologies and struggle to fully utilize existing ones, as they lack the necessary internal expertise for comprehensive security testing, code analysis, and continuous vulnerability management throughout the software development lifecycle.Key Market Trends
The Global Application Security Market is significantly shaped by the widespread adoption of Shift-Left Security Integration. This trend emphasizes embedding security practices and tools into the earliest phases of the software development lifecycle, moving security from a post-development gate to a continuous, integrated process. This proactive approach aims to identify and remediate vulnerabilities when they are less costly and complex to fix, streamlining development workflows and reducing overall risk exposure. According to the SANS Institute in October 2025, industry data indicates that false positives from traditional application security scanners frequently surpass 70 to 90 percent, demonstrating the critical need for earlier detection and validation to enhance efficiency and accuracy in security efforts.Key Market Players Profiled:
- IBM Corporation
- Cisco Systems, Inc
- Microsoft Corporation
- Check Point Software Technologies Ltd
- Palo Alto Networks, Inc
- Fortinet, Inc
- Open Text Corporation
- Hewlett Packard Enterprise
- Veracode, Inc
- Qualys, Inc.
Report Scope:
In this report, the Global Application Security Market has been segmented into the following categories:By Type:
- Web Application Security
- Mobile Application Security
By Component:
- Solution
- Services
By Application:
- BFSI
- Healthcare
- IT & Telecom
- Manufacturing
- Government
- Others
By Region:
- North America
- Europe
- Asia Pacific
- South America
- Middle East & Africa
Competitive Landscape
Company Profiles: Detailed analysis of the major companies present in the Global Application Security Market.Available Customizations:
With the given market data, the publisher offers customizations according to a company's specific needs. The following customization options are available for the report:- Detailed analysis and profiling of additional market players (up to five).
This product will be delivered within 1-3 business days.
Table of Contents
Companies Mentioned
- IBM Corporation
- Cisco Systems, Inc
- Microsoft Corporation
- Check Point Software Technologies Ltd
- Palo Alto Networks, Inc
- Fortinet, Inc
- Open Text Corporation
- Hewlett Packard Enterprise
- Veracode, Inc
- Qualys, Inc.
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 186 |
| Published | November 2025 |
| Forecast Period | 2024 - 2030 |
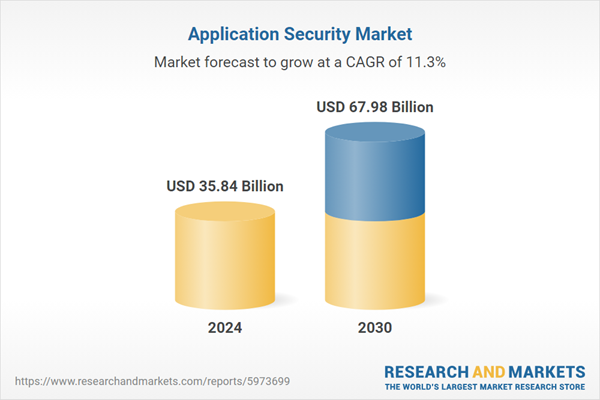
| Estimated Market Value ( USD | $ 35.84 Billion |
| Forecasted Market Value ( USD | $ 67.98 Billion |
| Compound Annual Growth Rate | 11.2% |
| Regions Covered | Global |
| No. of Companies Mentioned | 10 |