Large Enterprises is the fastest growing segment, North America is the largest market globally
Speak directly to the analyst to clarify any post sales queries you may have.
10% Free customizationThis report comes with 10% free customization, enabling you to add data that meets your specific business needs.
Key Market Drivers
The Global Security Information and Event Management Software Market growth is significantly influenced by the rising sophistication and frequency of cyber threats. Adversaries are continually developing advanced attack vectors, including zero-day exploits and highly targeted ransomware campaigns, which necessitate robust defense mechanisms. These evolving threats challenge traditional security perimeters, forcing organizations to adopt more comprehensive and analytical tools to detect and neutralize malicious activities effectively.Key Market Challenges
A significant impediment to the expansion of the Global Security Information and Event Management Software Market is the persistent shortage of skilled cybersecurity professionals. This deficiency directly hampers organizations' ability to effectively implement, manage, and optimize SIEM solutions, which are critical for comprehensive threat detection and incident response. Without adequately trained personnel, even the most advanced SIEM platforms can suffer from underutilization and lead to alert fatigue, diminishing their intended security benefits and return on investment.Key Market Trends
The adoption of cloud-native Security Information and Event Management (SIEM) solutions is a significant market trend, driven by the need for flexible, scalable, and cost-efficient security operations in cloud-centric IT environments. These solutions leverage cloud infrastructure benefits like elasticity and reduced operational overhead, proving more advantageous than traditional deployments. According to ISACA's 2024 Cloud Security Conference, over 80% of organizational resources are now hosted in the cloud, emphasizing the demand for cloud-native security. This is reflected in Microsoft's September 2025 announcement of the general availability of the Microsoft Sentinel data lake, offering a purpose-built, cloud-native foundation for security data management and analytics within its SIEM platform.Key Market Players Profiled:
- IBM Corporation
- Splunk, Inc.
- Fortinet, Inc.
- LogRhythm, Inc.
- Rapid7, Inc.
- Exabeam, Inc.
- Securonix, Inc.
- Fortra, LLC
- Graylog, Inc.
- Open Text Corporation
Report Scope:
In this report, the Global Security Information and Event Management Software Market has been segmented into the following categories:By Component:
- Solution
- Service
By Application:
- Log Management and Reporting
- Threat Intelligence
- Security Analytics
- Others
By Organization Size:
- Large Enterprises
- SMEs
By Deployment Mode:
- On-premises
- Cloud
By Vertical:
- IT & Telecom
- BFSI
- Healthcare
- Retail
- Manufacturing
- Utilities
- Others
By Region:
- North America
- Europe
- South America
- Middle East & Africa
- Asia Pacific
Competitive Landscape
Company Profiles: Detailed analysis of the major companies present in the Global Security Information and Event Management Software Market.Available Customizations:
With the given market data, the publisher offers customizations according to a company's specific needs. The following customization options are available for the report:- Detailed analysis and profiling of additional market players (up to five).
This product will be delivered within 1-3 business days.
Table of Contents
Companies Mentioned
- IBM Corporation
- Splunk, Inc.
- Fortinet, Inc.
- LogRhythm, Inc.
- Rapid7, Inc.
- Exabeam, Inc.
- Securonix, Inc.
- Fortra, LLC
- Graylog, Inc.
- Open Text Corporation
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 185 |
| Published | November 2025 |
| Forecast Period | 2024 - 2030 |
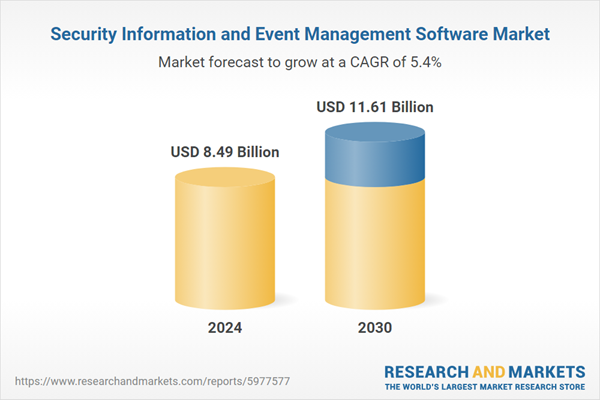
| Estimated Market Value ( USD | $ 8.49 Billion |
| Forecasted Market Value ( USD | $ 11.61 Billion |
| Compound Annual Growth Rate | 5.3% |
| Regions Covered | Global |
| No. of Companies Mentioned | 10 |