The Brazil market dominated the LAMEA Others Market by Country in 2023, and would continue to be a dominant market till 2031; thereby, achieving a market value of $136.5 million by 2031. The Argentina market is showcasing a CAGR of 27.2% during (2024 - 2031). Additionally, The UAE market would register a CAGR of 25.9% during (2024 - 2031).
ITDR solutions are widely adopted across various industries, including finance, healthcare, retail, and government. The financial sector, in particular, has been a significant adopter of ITDR solutions due to the high value of financial data and the stringent regulatory environment. Similarly, the healthcare industry increasingly adopts ITDR solutions to protect sensitive patient data and comply with regulations like the Health Insurance Portability and Accountability Act (HIPAA).
The rise of e-commerce and digital payment methods has made identity protection a top priority in the retail sector. Retailers implement ITDR solutions to secure customer data and prevent identity theft and fraud. Government agencies are also allocating resources towards the implementation of ITDR solutions in order to safeguard sensitive data and guarantee the integrity of public services.
In the Middle East, countries like the United Arab Emirates (UAE) and Saudi Arabia are investing heavily in digital infrastructure, leading to a growing reliance on digital technologies. According to the National Cybersecurity Authority, Saudi Arabia faced over 7 million cyber-attacks in 2022, underscoring the need for advanced identity threat detection capabilities. The Saudi Arabian Monetary Authority (SAMA) and the National Cybersecurity Authority have issued stringent guidelines and regulations to enhance data protection and cybersecurity measures, encouraging the adoption of ITDR solutions. Similarly, the UAE Cybersecurity Council reported a 250% increase in cyber-attacks in 2022 compared to the previous year, highlighting the critical need for ITDR solutions. The rapid digital transformation in finance, healthcare, and government sectors has also contributed to the rising demand for ITDR in these nations as these industries seek to secure digital identities against evolving cyber threats. Therefore, as regional organizations continue to embrace digital technologies, the demand for ITDR solutions is expected to increase further in the coming years.
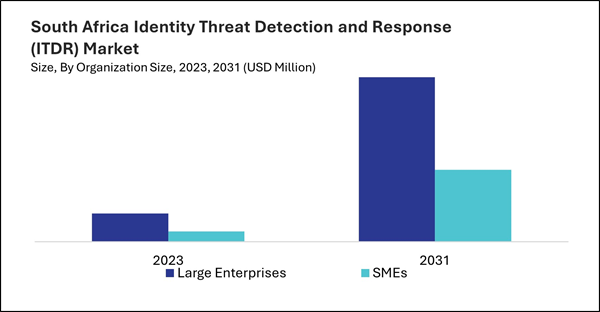
Based on Deployment Mode, the market is segmented into Cloud and On-premise. Based on Offering, the market is segmented into Solution (Credential Threat Protection, Active Directory Threat Management, Exposure Management, and Response & Remediation Management) and Services (Professional Services and Managed Security Services). Based on Organization Size, the market is segmented into Large Enterprises and SMEs. Based on Vertical, the market is segmented into BFSI, Government & Defense, Energy & Utilities, IT & ITeS, Telecommunication, Education, Retail & eCommerce, Healthcare & Lifesciences, and Others. Based on countries, the market is segmented into Brazil, Argentina, UAE, Saudi Arabia, South Africa, Nigeria, and Rest of LAMEA.
List of Key Companies Profiled
- Microsoft Corporation
- IBM Corporation
- Crowdstrike Holdings, Inc
- Zscaler, Inc
- Tenable Holdings, Inc.
- BeyondTrust Corporation
- CyberArk Software Ltd.
- Acalvio Technologies, Inc.
- Proofpoint, Inc. (Thoma Bravo)
- Semperis Technologies Inc.
Market Report Segmentation
By Deployment Mode- Cloud
- On-premise
- Solution
- Credential Threat Protection
- Active Directory Threat Management
- Exposure Management
- Response & Remediation Management
- Services
- Professional Services
- Managed Security Services
- Large Enterprises
- SMEs
- BFSI
- Government & Defense
- Energy & Utilities
- IT & ITeS
- Telecommunication
- Education
- Retail & eCommerce
- Healthcare & Lifesciences
- Others
- Brazil
- Argentina
- UAE
- Saudi Arabia
- South Africa
- Nigeria
- Rest of LAMEA
Table of Contents
Companies Mentioned
- Microsoft Corporation
- IBM Corporation
- Crowdstrike Holdings, Inc
- Zscaler, Inc
- Tenable Holdings, Inc.
- BeyondTrust Corporation
- CyberArk Software Ltd.
- Acalvio Technologies, Inc.
- Proofpoint, Inc. (Thoma Bravo)
- Semperis Technologies Inc.