The Brazil market dominated the LAMEA Cybersecurity in Critical Infrastructure Market by country in 2023, and is expected to continue to be a dominant market till 2031; thereby, achieving a market value of $590 million by 2031. The Argentina market is showcasing a CAGR of 7.1% during 2024-2031. Additionally, the UAE market would register a CAGR of 4.6% during 2024-2031.
The digital transformation of critical infrastructure is revolutionizing essential sectors like energy, healthcare, transportation, and water management through advanced technologies such as cloud computing, artificial intelligence (AI), and edge computing. Cloud platforms enable efficient storage and real-time access to operational data, allowing organizations to optimize performance and reduce costs.
AI and edge computing enhance critical infrastructure by enabling predictive analytics, anomaly detection, and real-time decision-making. In transportation, the city of Los Angeles utilizes artificial intelligence-driven traffic management systems to enhance traffic flow and mitigate congestion. Concurrently, Siemens implements AI technology within energy infrastructure to forecast and avert potential disruptions.
In Africa, Nigeria, the continent’s largest oil producer, faces persistent challenges in protecting its oil and gas infrastructure from physical and cyber threats. Frequent attacks on pipelines and installations in the Niger Delta highlight the region’s vulnerabilities. To counter these risks, the Nigerian government has enacted the Nigerian Hydrocarbon and Gas Industry Content Development (NOGICD) Act, which includes provisions for securing hydrocarbon infrastructure. The Nigerian Navy and the Joint Task Force (JTF) protect offshore platforms and pipelines. At the same time, cybersecurity efforts are being ramped up to address the growing risks of digital attacks on energy systems. Therefore, as countries across the LAMEA region recognize the importance of securing their energy assets against physical and cyber threats, the demand for critical infrastructure cybersecurity solutions is expected to experience substantial growth.
List of Key Companies Profiled
- Cisco Systems, Inc.
- IBM Corporation
- Fortinet, Inc.
- Palo Alto Networks, Inc.
- Check Point Software Technologies Ltd.
- Trend Micro, Inc.
- Huawei Technologies Co., Ltd. (Huawei Investment & Holding Co., Ltd.)
- Broadcom, Inc.
- Schneider Electric SE
- Honeywell International, Inc.
Market Report Segmentation
By Type- Network Access Control & Firewalls
- Encryption
- Threat Intelligence
- Other Type
- Government & Defense
- BFSI
- Energy & Power
- Transport & Logistics
- Commercial Sector
- Other Application
- Brazil
- Argentina
- UAE
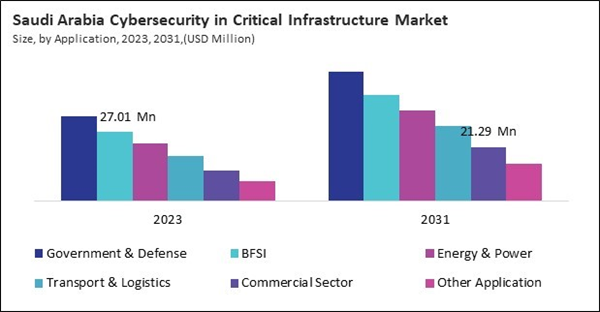
- Saudi Arabia
- South Africa
- Nigeria
- Rest of LAMEA
Table of Contents
Companies Mentioned
- Cisco Systems, Inc.
- IBM Corporation
- Fortinet, Inc.
- Palo Alto Networks, Inc.
- Check Point Software Technologies Ltd.
- Trend Micro, Inc.
- Huawei Technologies Co., Ltd. (Huawei Investment & Holding Co., Ltd.)
- Broadcom, Inc.
- Schneider Electric SE
- Honeywell International, Inc.