The China market dominated the Asia Pacific Cybersecurity in Critical Infrastructure Market by country in 2023, and is expected to continue to be a dominant market till 2031; thereby, achieving a market value of $2.19 billion by 2031. The Japan market is registering a CAGR of 4% during 2024-2031. Additionally, the India market is expected to showcase a CAGR of 5.4% during 2024-2031.
Regulatory frameworks and compliance requirements are driving the adoption of cybersecurity solutions in critical infrastructure. Governments all over are putting policies and standards in place to protect the security and reliability of vital services. These regulations incentivize organizations to invest in cybersecurity, creating a robust demand for solutions that meet compliance requirements.
The market for cybersecurity in critical infrastructure is also benefiting from significant investments in research and development. Governments and private enterprises are allocating resources to develop next-generation security technologies, including quantum encryption, blockchain, and zero-trust architectures. Quantum encryption offers unparalleled security by leveraging the principles of quantum mechanics, making it virtually impossible for attackers to intercept or manipulate data.
Australia’s focus on securing its energy infrastructure is evident in projects like the Gorgon LNG Project, one of the largest natural gas initiatives globally. Collaborative efforts between the government and private stakeholders have led to deploying sophisticated cybersecurity systems to protect critical energy assets from hacking and sabotage. Initiatives by the Critical Infrastructure Centre and the Trusted Information Sharing Network (TISN), along with the application of the Security of Critical Infrastructure (SOCI) Act, ensure compliance with stringent cybersecurity standards. The Asia Pacific region’s proactive cybersecurity measures are transforming it into a hub for critical infrastructure protection solutions. Governments and private stakeholders across India, Australia, China, and Japan are prioritizing advanced cybersecurity frameworks, real-time monitoring systems, and robust regulatory compliance to secure vital sectors. These efforts enhance the resilience of critical systems and position the region as a leader in addressing global cybersecurity challenges in critical infrastructure.
List of Key Companies Profiled
- Cisco Systems, Inc.
- IBM Corporation
- Fortinet, Inc.
- Palo Alto Networks, Inc.
- Check Point Software Technologies Ltd.
- Trend Micro, Inc.
- Huawei Technologies Co., Ltd. (Huawei Investment & Holding Co., Ltd.)
- Broadcom, Inc.
- Schneider Electric SE
- Honeywell International, Inc.
Market Report Segmentation
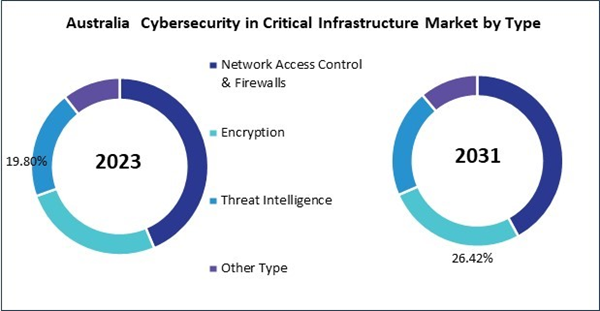
By Type- Network Access Control & Firewalls
- Encryption
- Threat Intelligence
- Other Type
- Government & Defense
- BFSI
- Energy & Power
- Transport & Logistics
- Commercial Sector
- Other Application
- China
- Japan
- India
- South Korea
- Australia
- Malaysia
- Rest of Asia Pacific
Table of Contents
Companies Mentioned
- Cisco Systems, Inc.
- IBM Corporation
- Fortinet, Inc.
- Palo Alto Networks, Inc.
- Check Point Software Technologies Ltd.
- Trend Micro, Inc.
- Huawei Technologies Co., Ltd. (Huawei Investment & Holding Co., Ltd.)
- Broadcom, Inc.
- Schneider Electric SE
- Honeywell International, Inc.