Identity Security Posture Management (ISPM): Why Is It the Next Strategic Pillar in Cybersecurity?
Global Identity Security Posture Management Market - Key Trends & Drivers Summarized
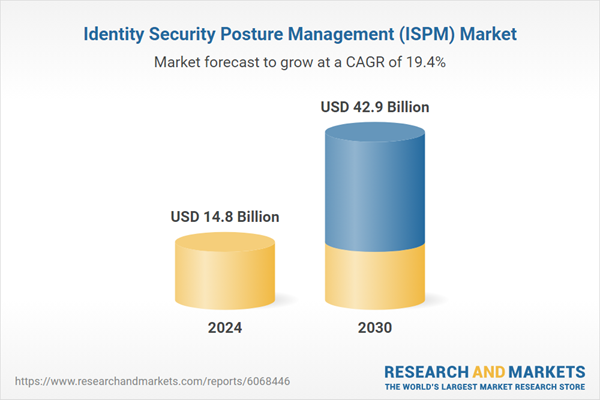
The global Identity Security Posture Management (ISPM) market is gaining rapid momentum as enterprises face increasing pressure to secure complex, hybrid digital environments against identity-based cyber threats. ISPM refers to the continuous monitoring, assessment, and remediation of identity and access-related risks across an organization's IT ecosystem. Unlike traditional identity and access management (IAM) tools that focus on provisioning and authentication, ISPM solutions provide a holistic, risk-driven approach to managing identity security posture. This includes identifying privilege escalation paths, detecting excessive entitlements, enforcing least-privilege access, and continuously validating identity configurations in line with compliance mandates.The market’ s growth is fueled by the growing sophistication of identity-based attacks, especially in cloud-native environments where misconfigured identities and over-provisioned roles often become prime attack vectors. With identities now representing the new security perimeter - particularly in remote work setups, multi-cloud infrastructures, and zero-trust architectures - enterprises are realizing that legacy IAM tools alone are insufficient. Regulatory frameworks such as GDPR, HIPAA, and the SEC’ s cyber disclosure rules are also pushing companies to strengthen their identity governance and reporting capabilities. As such, ISPM is becoming an essential layer within the modern cybersecurity stack, offering real-time visibility and actionable intelligence to mitigate identity-driven risk across IT, OT, and cloud domains.
How Is Technology Enabling a New Generation of Identity Risk Mitigation?
The evolution of ISPM is closely linked to advancements in automation, AI, and cloud-native security tooling. Modern ISPM platforms leverage machine learning to analyze user behavior, detect anomalies, and identify toxic permission combinations that could lead to lateral movement or privilege misuse. These systems continuously scan cloud and on-prem environments - including AWS IAM policies, Azure AD configurations, and SaaS entitlements - to generate dynamic risk scores, prioritize threats, and recommend remediation paths. Integration with Security Information and Event Management (SIEM) and Security Orchestration, Automation and Response (SOAR) platforms further enhances the operationalization of identity insights, allowing faster response to real-time threats.Another key innovation is the use of graph-based modeling to map identity relationships and access pathways across the enterprise. This enables security teams to understand complex privilege hierarchies, identify orphaned accounts, and expose excessive permissions at a granular level. Moreover, automated policy enforcement mechanisms allow organizations to remediate misconfigurations and revert risky access changes without manual intervention. The rise of Infrastructure-as-Code (IaC) security and API-driven access governance is also fueling ISPM adoption in DevOps and DevSecOps pipelines, ensuring that identity risks are addressed early in the development lifecycle. Together, these technologies are transforming ISPM into a proactive, intelligence-driven framework for identity risk governance.
Where Is Demand for ISPM Surging - And Who Are the Key Stakeholders?
The demand for ISPM solutions is surging across all major geographies, with North America leading due to early cloud adoption, stringent compliance requirements, and high levels of cybersecurity maturity. Europe follows closely, driven by GDPR and increasing concern over cross-border data access and third-party risk. The Asia-Pacific region is emerging as a high-growth market, propelled by digital transformation initiatives, growing cloud adoption, and an expanding attack surface across fintech, healthcare, and telecom sectors. Latin America and the Middle East are also showing signs of rising ISPM adoption, particularly in critical infrastructure sectors and multinational enterprises operating across diverse regulatory landscapes.Key stakeholders driving adoption include Chief Information Security Officers (CISOs), Identity and Access Management (IAM) teams, Cloud Security Architects, and compliance officers. Organizations with large user bases, extensive third-party integrations, and complex multi-cloud environments - such as financial institutions, healthcare providers, and technology companies - are among the earliest adopters. Additionally, managed security service providers (MSSPs) and system integrators are incorporating ISPM capabilities into their security service offerings to meet rising client expectations for end-to-end identity risk visibility and mitigation. The demand is particularly acute in sectors handling sensitive data, where breaches tied to identity compromise can result in severe reputational and regulatory repercussions.
The Growth in the Identity Security Posture Management Market Is Driven by Several Factors…
The growth in the Identity Security Posture Management market is driven by several factors linked to emerging threat vectors, evolving enterprise architectures, and changing regulatory expectations. Chief among them is the exponential increase in cloud workloads and the decentralized nature of identity across hybrid and multi-cloud infrastructures. As identities span SaaS apps, cloud platforms, DevOps pipelines, and on-prem resources, the attack surface becomes harder to manage, making ISPM critical for continuous visibility and control.Another major driver is the rise in credential-based attacks and privilege misuse, which have become dominant tactics in modern cyber breaches. ISPM tools provide automated, contextual analysis to prevent such exploits by enforcing least-privilege access and detecting misconfigurations before they are exploited. Additionally, the proliferation of machine and non-human identities - such as APIs, service accounts, and bots - is adding layers of complexity that traditional IAM tools cannot handle alone. ISPM addresses this gap with deep entitlements management and identity lifecycle analytics.
Regulatory compliance is also a powerful growth enabler. New mandates increasingly require organizations to demonstrate proactive identity risk management and provide audit trails for privileged access. ISPM platforms fulfill these mandates by offering real-time posture assessments and compliance reporting. Lastly, the growing shift toward zero-trust security frameworks is solidifying ISPM’ s role as a foundational control layer. By providing continuous identity verification, behavior-based risk scoring, and policy enforcement, ISPM aligns seamlessly with zero-trust principles - ensuring that the right identities access the right resources under the right conditions at all times.
Report Scope
The report analyzes the Identity Security Posture Management (ISPM) market, presented in terms of market value. The analysis covers the key segments and geographic regions outlined below.- Segments: Offering (Solutions Offering, Services Offering); Deployment (On-Premise Deployment, Cloud Deployment); Vertical (Introduction Vertical, BFSI Vertical, Retail & Ecommerce Vertical, Government & Defense Vertical, Gaming & Gambling Vertical, IT & ITES Vertical, Telecom Vertical, Energy & Utilities Vertical, Education Vertical, Healthcare & Life Sciences Vertical, Other Verticals).
- Geographic Regions/Countries: World; United States; Canada; Japan; China; Europe (France; Germany; Italy; United Kingdom; and Rest of Europe); Asia-Pacific; Rest of World.
Key Insights:
- Market Growth: Understand the significant growth trajectory of the Solutions Component segment, which is expected to reach US$27.2 Billion by 2030 with a CAGR of a 17.7%. The Services Component segment is also set to grow at 22.9% CAGR over the analysis period.
- Regional Analysis: Gain insights into the U.S. market, valued at $3.9 Billion in 2024, and China, forecasted to grow at an impressive 18.4% CAGR to reach $6.6 Billion by 2030. Discover growth trends in other key regions, including Japan, Canada, Germany, and the Asia-Pacific.
Why You Should Buy This Report:
- Detailed Market Analysis: Access a thorough analysis of the Global Identity Security Posture Management (ISPM) Market, covering all major geographic regions and market segments.
- Competitive Insights: Get an overview of the competitive landscape, including the market presence of major players across different geographies.
- Future Trends and Drivers: Understand the key trends and drivers shaping the future of the Global Identity Security Posture Management (ISPM) Market.
- Actionable Insights: Benefit from actionable insights that can help you identify new revenue opportunities and make strategic business decisions.
Key Questions Answered:
- How is the Global Identity Security Posture Management (ISPM) Market expected to evolve by 2030?
- What are the main drivers and restraints affecting the market?
- Which market segments will grow the most over the forecast period?
- How will market shares for different regions and segments change by 2030?
- Who are the leading players in the market, and what are their prospects?
Report Features:
- Comprehensive Market Data: Independent analysis of annual sales and market forecasts in US$ Million from 2024 to 2030.
- In-Depth Regional Analysis: Detailed insights into key markets, including the U.S., China, Japan, Canada, Europe, Asia-Pacific, Latin America, Middle East, and Africa.
- Company Profiles: Coverage of players such as CyberArk Software Ltd., Delinea, Evidian SA, Fortra, Imprivata, Inc. and more.
- Complimentary Updates: Receive free report updates for one year to keep you informed of the latest market developments.
Some of the 34 companies featured in this Identity Security Posture Management (ISPM) market report include:
- BeyondTrust Corporation
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- CrowdStrike Holdings, Inc.
- CyberArk Software Ltd.
- Delinea Inc.
- ManageEngine (a division of Zoho Corp.)
- Mesh Security
- Microsoft Corporation
- Okta, Inc.
- One Identity LLC
- Oracle Corporation
- Palo Alto Networks, Inc.
- Ping Identity Holding Corp.
- PlainID
- Radiant Logic, Inc.
- SailPoint Technologies Holdings, Inc.
- Silverfort
- Trend Micro Incorporated
- Veza
This edition integrates the latest global trade and economic shifts into comprehensive market analysis. Key updates include:
- Tariff and Trade Impact: Insights into global tariff negotiations across 180+ countries, with analysis of supply chain turbulence, sourcing disruptions, and geographic realignment. Special focus on 2025 as a pivotal year for trade tensions, including updated perspectives on the Trump-era tariffs.
- Adjusted Forecasts and Analytics: Revised global and regional market forecasts through 2030, incorporating tariff effects, economic uncertainty, and structural changes in globalization. Includes historical analysis from 2015 to 2023.
- Strategic Market Dynamics: Evaluation of revised market prospects, regional outlooks, and key economic indicators such as population and urbanization trends.
- Innovation & Technology Trends: Latest developments in product and process innovation, emerging technologies, and key industry drivers shaping the competitive landscape.
- Competitive Intelligence: Updated global market share estimates for 2025, competitive positioning of major players (Strong/Active/Niche/Trivial), and refined focus on leading global brands and core players.
- Expert Insight & Commentary: Strategic analysis from economists, trade experts, and domain specialists to contextualize market shifts and identify emerging opportunities.
Table of Contents
Companies Mentioned (Partial List)
A selection of companies mentioned in this report includes, but is not limited to:
- BeyondTrust Corporation
- Check Point Software Technologies Ltd.
- Cisco Systems, Inc.
- CrowdStrike Holdings, Inc.
- CyberArk Software Ltd.
- Delinea Inc.
- ManageEngine (a division of Zoho Corp.)
- Mesh Security
- Microsoft Corporation
- Okta, Inc.
- One Identity LLC
- Oracle Corporation
- Palo Alto Networks, Inc.
- Ping Identity Holding Corp.
- PlainID
- Radiant Logic, Inc.
- SailPoint Technologies Holdings, Inc.
- Silverfort
- Trend Micro Incorporated
- Veza
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 172 |
| Published | January 2026 |
| Forecast Period | 2024 - 2030 |
| Estimated Market Value ( USD | $ 14.8 Billion |
| Forecasted Market Value ( USD | $ 42.9 Billion |
| Compound Annual Growth Rate | 19.4% |
| Regions Covered | Global |