Global Serverless Security Market - Key Trends & Drivers Summarized
Is Serverless Architecture Redefining the Cybersecurity Rulebook?
The rise of serverless computing is transforming how applications are built and deployed - but it's also rewriting the playbook for cloud security. Unlike traditional server-based models where organizations manage operating systems and runtime environments, serverless architecture offloads infrastructure management to cloud providers. While this simplifies development and scalability, it introduces new complexities and vulnerabilities unique to function-based deployments. In serverless environments, the attack surface expands across multiple discrete functions, APIs, and event triggers, making it harder to monitor and protect. Traditional perimeter-based security models struggle to provide visibility in ephemeral, stateless architectures where functions may execute in milliseconds and vanish. Moreover, since serverless functions often rely heavily on third-party services, libraries, and APIs, the risk of supply chain vulnerabilities, insecure dependencies, and misconfigured permissions increases substantially. These shifting dynamics are forcing cybersecurity teams to rethink their strategies - focusing on identity and access management (IAM), zero-trust policies, API protection, and real-time threat detection tailored to serverless environments.How Are Evolving Threat Vectors Driving the Need for Specialized Security Frameworks?
With serverless adoption growing across industries, so too is the sophistication of threat vectors targeting function-based workloads. Threat actors are exploiting blind spots such as insecure event triggers, excessive permissions, unvalidated inputs, and vulnerable open-source libraries used within serverless functions. Additionally, cold starts and runtime execution time limits introduce performance trade-offs that can be exploited to trigger denial-of-service attacks. New forms of injection attacks - such as function event injection and deserialization attacks - are emerging, exploiting the stateless nature of serverless applications and their reliance on APIs and external triggers. Because traditional security tools like firewalls, antivirus, and agent-based monitoring cannot operate effectively in serverless environments, there's an urgent demand for security frameworks designed specifically for serverless contexts. These include function-level scanning, runtime behavior analysis, policy-as-code for IAM controls, and automated vulnerability management integrated into CI/CD pipelines. Major cloud providers are also enhancing native serverless security features - such as AWS Lambda's IAM roles, VPC integration, and secrets management - while third-party security vendors are innovating with function observability, least-privilege access automation, and anomaly detection tailored to micro-runtime behavior.Can DevSecOps and Policy Automation Solve the Serverless Security Puzzle?
The ephemeral, highly distributed nature of serverless computing demands a paradigm shift toward DevSecOps - the integration of security directly into the development and deployment lifecycle. This approach empowers development teams to build secure functions from the ground up, using tools that automatically scan for misconfigurations, insecure dependencies, and policy violations before deployment. Policy-as-code and infrastructure-as-code tools such as Terraform, Pulumi, and Open Policy Agent (OPA) are gaining momentum, allowing security rules to be embedded and enforced within automated deployment pipelines. These tools help ensure that serverless applications adhere to compliance requirements, such as GDPR, HIPAA, and SOC 2, without slowing down development velocity. Furthermore, the serverless security ecosystem is evolving with solutions offering continuous monitoring of function behavior, alerting on deviations from known baselines, and integrating threat intelligence to preempt novel attack vectors. As multi-cloud and hybrid cloud strategies gain traction, cross-platform visibility and policy consistency are becoming critical, leading to the emergence of centralized serverless security management platforms that bridge the gap across cloud environments. Ultimately, solving the serverless security puzzle lies in creating seamless collaboration between developers, security teams, and automation tools.What's Fueling the Growth of the Serverless Security Market?
The growth in the serverless security market is driven by several factors directly related to technology adoption, evolving threat landscapes, and enterprise cloud strategies. First, the rapid rise of serverless computing across startups, enterprises, and public sector organizations is increasing the number of serverless deployments, expanding the attack surface and necessitating new security measures. Second, the growing use of APIs, third-party integrations, and microservices within serverless applications is raising concerns around access control, data leakage, and inter-service trust. Third, as development lifecycles become shorter and more agile, organizations are prioritizing security automation and continuous compliance - driving demand for tools that embed security into CI/CD workflows. Fourth, increasing awareness of new serverless-specific attack types such as event injection, insecure function triggers, and privilege escalation is pushing CISOs and security architects to invest in specialized protection and observability tools. Fifth, major cloud service providers are enhancing their security offerings, but enterprise customers are seeking vendor-agnostic solutions to maintain consistency across multi-cloud and hybrid environments. Sixth, regulatory scrutiny and data protection laws are putting pressure on organizations to demonstrate robust security across all cloud-native workloads - including serverless functions. Finally, the shift toward zero-trust architecture and least-privilege access control is accelerating the development and adoption of identity-first security models purpose-built for serverless environments. These drivers collectively underline why serverless security is fast emerging as a critical pillar in the broader cloud security market.Report Scope
The report analyzes the Serverless Security market, presented in terms of market value (US$). The analysis covers the key segments and geographic regions outlined below:- Segments: Service Model (Function as a Service, Backend as a Service); Security Type (Data Security, Network Security, Application Security, Perimeter Security, Others); Deployment (Cloud, On-Premise); End-Use (BFSI, Healthcare, Retail & E-Commerce, IT & Telecommunications, Government & Public Sector, Manufacturing, Energy & Utilities, Others).
- Geographic Regions/Countries: World; United States; Canada; Japan; China; Europe (France; Germany; Italy; United Kingdom; Spain; Russia; and Rest of Europe); Asia-Pacific (Australia; India; South Korea; and Rest of Asia-Pacific); Latin America (Argentina; Brazil; Mexico; and Rest of Latin America); Middle East (Iran; Israel; Saudi Arabia; United Arab Emirates; and Rest of Middle East); and Africa.
Key Insights:
- Market Growth: Understand the significant growth trajectory of the Function as a Service segment, which is expected to reach US$6.7 Billion by 2030 with a CAGR of a 24.9%. The Backend as a Service segment is also set to grow at 31.5% CAGR over the analysis period.
- Regional Analysis: Gain insights into the U.S. market, valued at $757.2 Million in 2024, and China, forecasted to grow at an impressive 35.7% CAGR to reach $2.9 Billion by 2030. Discover growth trends in other key regions, including Japan, Canada, Germany, and the Asia-Pacific.
Why You Should Buy This Report:
- Detailed Market Analysis: Access a thorough analysis of the Global Serverless Security Market, covering all major geographic regions and market segments.
- Competitive Insights: Get an overview of the competitive landscape, including the market presence of major players across different geographies.
- Future Trends and Drivers: Understand the key trends and drivers shaping the future of the Global Serverless Security Market.
- Actionable Insights: Benefit from actionable insights that can help you identify new revenue opportunities and make strategic business decisions.
Key Questions Answered:
- How is the Global Serverless Security Market expected to evolve by 2030?
- What are the main drivers and restraints affecting the market?
- Which market segments will grow the most over the forecast period?
- How will market shares for different regions and segments change by 2030?
- Who are the leading players in the market, and what are their prospects?
Report Features:
- Comprehensive Market Data: Independent analysis of annual sales and market forecasts in US$ Million from 2024 to 2030.
- In-Depth Regional Analysis: Detailed insights into key markets, including the U.S., China, Japan, Canada, Europe, Asia-Pacific, Latin America, Middle East, and Africa.
- Company Profiles: Coverage of players such as Akamai, Alibaba Cloud, Amazon Web Services (AWS), Backendless, Cloudflare and more.
- Complimentary Updates: Receive free report updates for one year to keep you informed of the latest market developments.
Some of the 36 companies featured in this Serverless Security market report include:
- Alibaba Cloud
- Amazon Web Services (AWS)
- Aqua Security
- CA Technologies (Broadcom Inc.)
- Check Point Software Technologies
- Cisco Systems, Inc.
- Cloudflare
- CrowdStrike
- Datadog
- Fortinet, Inc.
- Google LLC
- IBM Corporation
- Imperva
- Lacework
- Microsoft Corporation
- Netskope
- Oracle Corporation
- Palo Alto Networks
- Proofpoint
- Protego Labs
- Qualys
- Rackspace Technology
- Sonrai Security
- StackHawk
- Symantec Corporation (Broadcom Inc.)
- Syncano
- Thundra
- Trend Micro
- Wiz
- Zscaler
This edition integrates the latest global trade and economic shifts into comprehensive market analysis. Key updates include:
- Tariff and Trade Impact: Insights into global tariff negotiations across 180+ countries, with analysis of supply chain turbulence, sourcing disruptions, and geographic realignment. Special focus on 2025 as a pivotal year for trade tensions, including updated perspectives on the Trump-era tariffs.
- Adjusted Forecasts and Analytics: Revised global and regional market forecasts through 2030, incorporating tariff effects, economic uncertainty, and structural changes in globalization. Includes historical analysis from 2015 to 2023.
- Strategic Market Dynamics: Evaluation of revised market prospects, regional outlooks, and key economic indicators such as population and urbanization trends.
- Innovation & Technology Trends: Latest developments in product and process innovation, emerging technologies, and key industry drivers shaping the competitive landscape.
- Competitive Intelligence: Updated global market share estimates for 2025, competitive positioning of major players (Strong/Active/Niche/Trivial), and refined focus on leading global brands and core players.
- Expert Insight & Commentary: Strategic analysis from economists, trade experts, and domain specialists to contextualize market shifts and identify emerging opportunities.
Table of Contents
Companies Mentioned (Partial List)
A selection of companies mentioned in this report includes, but is not limited to:
- Alibaba Cloud
- Amazon Web Services (AWS)
- Aqua Security
- CA Technologies (Broadcom Inc.)
- Check Point Software Technologies
- Cisco Systems, Inc.
- Cloudflare
- CrowdStrike
- Datadog
- Fortinet, Inc.
- Google LLC
- IBM Corporation
- Imperva
- Lacework
- Microsoft Corporation
- Netskope
- Oracle Corporation
- Palo Alto Networks
- Proofpoint
- Protego Labs
- Qualys
- Rackspace Technology
- Sonrai Security
- StackHawk
- Symantec Corporation (Broadcom Inc.)
- Syncano
- Thundra
- Trend Micro
- Wiz
- Zscaler
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 480 |
| Published | January 2026 |
| Forecast Period | 2024 - 2030 |
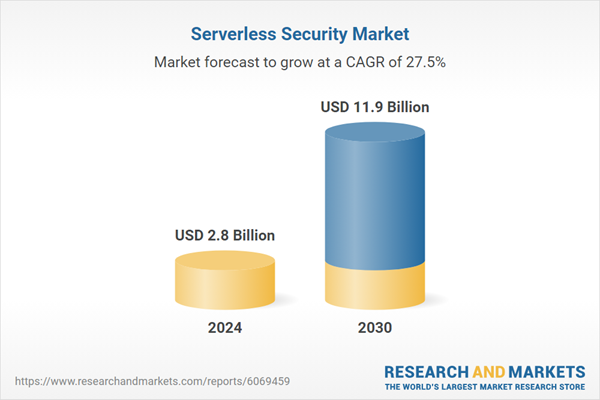
| Estimated Market Value ( USD | $ 2.8 Billion |
| Forecasted Market Value ( USD | $ 11.9 Billion |
| Compound Annual Growth Rate | 27.5% |
| Regions Covered | Global |