Global V2X Cybersecurity Market - Key Trends & Drivers Summarized
How Are Interconnected Vehicles Reshaping Security Priorities on the Roads?
The Vehicle-to-Everything (V2X) cybersecurity market is rapidly evolving as global transportation systems increasingly transition towards connected and autonomous mobility ecosystems. V2X technologies, encompassing Vehicle-to-Vehicle (V2V), Vehicle-to-Infrastructure (V2I), Vehicle-to-Network (V2N), and Vehicle-to-Pedestrian (V2P) communication protocols, have introduced immense opportunities to enhance traffic efficiency, safety, and mobility. However, this interconnected framework also introduces heightened vulnerabilities to cyber threats. Attack vectors such as man-in-the-middle attacks, spoofing, data tampering, and denial-of-service (DoS) attacks are becoming critical concerns. These threats can compromise driver safety, traffic systems, and even national security. Consequently, the demand for robust, end-to-end cybersecurity solutions has intensified. Security measures now focus on authentication protocols, secure software updates, intrusion detection systems (IDS), and Public Key Infrastructure (PKI) frameworks. The deployment of edge computing and AI-driven threat intelligence is further strengthening V2X defenses by enabling real-time risk mitigation. Regulations by bodies such as the European Union Agency for Cybersecurity (ENISA) and the U.S. National Highway Traffic Safety Administration (NHTSA) are shaping security frameworks and pushing OEMs to adopt secure-by-design principles. The integration of cybersecurity at every layer of vehicular communication has become essential as V2X systems become more complex and mission-critical.Why Is Regulatory Rigor Becoming the Backbone of V2X Cybersecurity Evolution?
Stringent regulatory environments are playing a pivotal role in driving the V2X cybersecurity landscape. In regions like Europe, the UN Regulation No. 155 mandates cybersecurity management systems (CSMS) as a prerequisite for type approval of vehicles. The UNECE WP.29 framework, requiring automakers to demonstrate compliance with cybersecurity lifecycle management and over-the-air update systems, has significantly raised the bar for manufacturers. In the U.S., the Department of Transportation (DoT) and the NHTSA are collaborating to establish V2X communication guidelines that prioritize secure communication protocols and data privacy. These frameworks are compelling industry stakeholders to collaborate with cybersecurity solution providers and standardization bodies like the IEEE, ETSI, and 5GAA. Furthermore, the rapid deployment of 5G networks and the advent of edge and cloud-native V2X platforms have added layers of complexity to compliance. Regulatory clarity is also pushing the development of digital twin-based simulations for cyber resilience testing. These standards are not only ensuring consistent protection across supply chains but are also fostering a competitive landscape where companies are differentiating themselves through compliance-readiness and proactive risk management. Additionally, as vehicles become more software-defined and connected to broader ecosystems including smart cities, regulators are pushing for continuous threat monitoring systems that go beyond the vehicle perimeter, integrating citywide IoT infrastructure cybersecurity.Can Next-Gen Technologies Disrupt the Status Quo in V2X Security Architectures?
Cutting-edge technologies are transforming the V2X cybersecurity paradigm with solutions that are more intelligent, adaptive, and decentralized. Artificial Intelligence (AI) and Machine Learning (ML) are enabling advanced threat detection systems that can learn from data patterns to predict and prevent attacks. Blockchain is gaining traction as a tamper-proof method for securing data exchanges and managing device identities in V2X ecosystems. Zero Trust Architecture (ZTA) is being increasingly adopted to minimize implicit trust zones within vehicular networks, ensuring that every data transaction is authenticated and encrypted. The integration of Secure Multi-party Computation (SMPC) and Homomorphic Encryption is addressing privacy challenges by enabling data processing without exposing raw data. Software-Defined Networking (SDN) and Network Function Virtualization (NFV) are enabling more scalable and programmable security frameworks that adjust to dynamic traffic conditions and risk profiles. Furthermore, quantum-resistant cryptographic techniques are being explored to future-proof V2X systems against the impending threats posed by quantum computing. Automotive OEMs and Tier 1 suppliers are investing heavily in cybersecurity R&D, establishing cyber fusion centers and testing labs to develop next-generation security platforms. As vehicles become part of a larger Mobility-as-a-Service (MaaS) ecosystem, securing edge devices, telematics control units (TCUs), and sensor networks is becoming crucial. These innovations are collectively redefining how security is embedded into the digital DNA of connected vehicles.What Forces Are Accelerating the Global Momentum in the V2X Cybersecurity Market?
The growth in the global V2X cybersecurity market is driven by several factors directly linked to evolving technology frameworks, dynamic end-use applications, and shifting consumer behavior. A key driver is the escalating adoption of autonomous and semi-autonomous vehicles that rely heavily on uninterrupted V2X communication, necessitating fortified cybersecurity infrastructure. The widespread rollout of 5G networks is amplifying data exchange capabilities, thereby expanding the attack surface and increasing the need for robust security mechanisms. The surge in electric vehicles (EVs), especially those integrated with cloud-connected ecosystems, is further elevating cybersecurity priorities. Automakers are under pressure to comply with evolving cyber regulations, leading to increased investment in embedded security systems from design to deployment. Another significant growth catalyst is the rise in consumer awareness regarding vehicle data privacy and digital safety, driving demand for transparency and real-time protection. The integration of V2X systems in commercial vehicle fleets and smart transportation grids is prompting large-scale deployments of secure communication platforms, especially in logistics, urban mobility, and emergency response services. Moreover, the expansion of smart city initiatives globally is aligning urban infrastructure with vehicular networks, creating a need for city-level cybersecurity frameworks. Collaborations between automotive manufacturers, telecom providers, and cybersecurity firms are also accelerating the development of unified, scalable, and adaptive security solutions. These market shifts, coupled with the evolution of attack methodologies and increasing financial losses from vehicular cyberattacks, are cementing cybersecurity as a critical pillar in the global V2X ecosystem.Report Scope
The report analyzes the V2X Cybersecurity market, presented in terms of market value (US$). The analysis covers the key segments and geographic regions outlined below:- Segments: Unit Type (On-board Units, Roadside Units); Connectivity (Dedicated Short Range Communications, Cellular); Communication (Vehicle-to-Vehicle, Vehicle-to-Infrastructure, Vehicle-to-Grid, Vehicle-to-Pedestrian, Vehicle-to-Cloud); Propulsion (ICE, Electric & Hybrid); End-Use (Passenger Cars, Commercial Vehicles).
- Geographic Regions/Countries: World; United States; Canada; Japan; China; Europe (France; Germany; Italy; United Kingdom; and Rest of Europe); Asia-Pacific; Rest of World.
Key Insights:
- Market Growth: Understand the significant growth trajectory of the On-board Units segment, which is expected to reach US$5.1 Billion by 2030 with a CAGR of a 17.1%. The Roadside Units segment is also set to grow at 21.9% CAGR over the analysis period.
- Regional Analysis: Gain insights into the U.S. market, valued at $810.5 Million in 2024, and China, forecasted to grow at an impressive 18% CAGR to reach $1.3 Billion by 2030. Discover growth trends in other key regions, including Japan, Canada, Germany, and the Asia-Pacific.
Why You Should Buy This Report:
- Detailed Market Analysis: Access a thorough analysis of the Global V2X Cybersecurity Market, covering all major geographic regions and market segments.
- Competitive Insights: Get an overview of the competitive landscape, including the market presence of major players across different geographies.
- Future Trends and Drivers: Understand the key trends and drivers shaping the future of the Global V2X Cybersecurity Market.
- Actionable Insights: Benefit from actionable insights that can help you identify new revenue opportunities and make strategic business decisions.
Key Questions Answered:
- How is the Global V2X Cybersecurity Market expected to evolve by 2030?
- What are the main drivers and restraints affecting the market?
- Which market segments will grow the most over the forecast period?
- How will market shares for different regions and segments change by 2030?
- Who are the leading players in the market, and what are their prospects?
Report Features:
- Comprehensive Market Data: Independent analysis of annual sales and market forecasts in US$ Million from 2024 to 2030.
- In-Depth Regional Analysis: Detailed insights into key markets, including the U.S., China, Japan, Canada, Europe, Asia-Pacific, Latin America, Middle East, and Africa.
- Company Profiles: Coverage of players such as Air Oasis LLC, Airpura Industries, AiroDoctor, Austin Air Systems, Biobase and more.
- Complimentary Updates: Receive free report updates for one year to keep you informed of the latest market developments.
Some of the 37 companies featured in this V2X Cybersecurity market report include:
- Aptiv PLC
- Argus Cyber Security
- AUTOCRYPT Co., Ltd.
- Autotalks Ltd.
- BlackBerry Certicom
- Cisco Systems, Inc.
- Continental AG
- DENSO Corporation
- ESCRYPT GmbH
- Green Hills Software
- Harman International
- Infineon Technologies AG
- Intel Corporation
- Karamba Security
- Lear Corporation
- NXP Semiconductors N.V.
- Qualcomm Technologies, Inc.
- SafeRide Technologies
- Trillium Secure Inc.
- Vector Informatik GmbH
This edition integrates the latest global trade and economic shifts into comprehensive market analysis. Key updates include:
- Tariff and Trade Impact: Insights into global tariff negotiations across 180+ countries, with analysis of supply chain turbulence, sourcing disruptions, and geographic realignment. Special focus on 2025 as a pivotal year for trade tensions, including updated perspectives on the Trump-era tariffs.
- Adjusted Forecasts and Analytics: Revised global and regional market forecasts through 2030, incorporating tariff effects, economic uncertainty, and structural changes in globalization. Includes historical analysis from 2015 to 2023.
- Strategic Market Dynamics: Evaluation of revised market prospects, regional outlooks, and key economic indicators such as population and urbanization trends.
- Innovation & Technology Trends: Latest developments in product and process innovation, emerging technologies, and key industry drivers shaping the competitive landscape.
- Competitive Intelligence: Updated global market share estimates for 2025, competitive positioning of major players (Strong/Active/Niche/Trivial), and refined focus on leading global brands and core players.
- Expert Insight & Commentary: Strategic analysis from economists, trade experts, and domain specialists to contextualize market shifts and identify emerging opportunities.
Table of Contents
Companies Mentioned (Partial List)
A selection of companies mentioned in this report includes, but is not limited to:
- Aptiv PLC
- Argus Cyber Security
- AUTOCRYPT Co., Ltd.
- Autotalks Ltd.
- BlackBerry Certicom
- Cisco Systems, Inc.
- Continental AG
- DENSO Corporation
- ESCRYPT GmbH
- Green Hills Software
- Harman International
- Infineon Technologies AG
- Intel Corporation
- Karamba Security
- Lear Corporation
- NXP Semiconductors N.V.
- Qualcomm Technologies, Inc.
- SafeRide Technologies
- Trillium Secure Inc.
- Vector Informatik GmbH
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 229 |
| Published | January 2026 |
| Forecast Period | 2024 - 2030 |
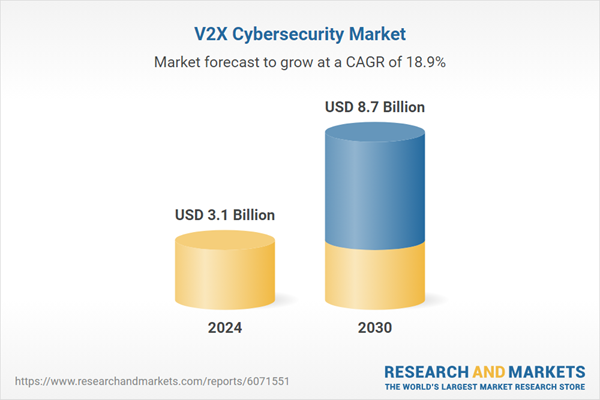
| Estimated Market Value ( USD | $ 3.1 Billion |
| Forecasted Market Value ( USD | $ 8.7 Billion |
| Compound Annual Growth Rate | 18.9% |
| Regions Covered | Global |