Global Hardware OTP Token Authentication Market - Key Trends and Drivers Summarized
Why Is Hardware OTP Token Authentication Becoming Essential for Secure Digital Access and Data Protection?
Hardware OTP (One-Time Password) token authentication has become an essential tool for securing digital access and protecting sensitive data in an increasingly connected world. But why is hardware OTP token authentication so critical today? With cyber threats on the rise, including phishing, hacking, and identity theft, businesses and individuals are prioritizing security measures that offer robust protection. OTP tokens provide an additional layer of security beyond traditional passwords by generating a unique, time-sensitive code that is used for authentication, ensuring that only authorized users can access accounts or systems.Unlike software-based solutions, hardware OTP tokens are physically separate from the devices they protect, making them resistant to malware attacks or hacking attempts. These tokens are commonly used in industries like finance, healthcare, and government, where the security of confidential data is paramount. As more businesses move operations online and adopt cloud services, the need for secure and reliable authentication methods is growing, positioning hardware OTP tokens as a crucial component in preventing unauthorized access and data breaches.
How Are Technological Advancements Improving the Security and Usability of Hardware OTP Tokens?
Technological advancements are significantly improving both the security and usability of hardware OTP tokens, making them more effective and user-friendly for a variety of applications. One of the most important advancements is the introduction of multi-factor authentication (MFA), which combines OTP tokens with other security factors, such as biometric verification or PIN codes. This layered approach ensures that even if one security factor is compromised, the system remains protected. By integrating OTP tokens with MFA, companies are providing a more secure authentication process, significantly reducing the risk of unauthorized access.Another key advancement is the development of more compact and durable hardware tokens. Early OTP tokens were often bulky and inconvenient to carry, but modern devices have become small, lightweight, and easy to use. Many OTP tokens now come with features like displays for easy reading of generated codes, buttons for interaction, and even USB or NFC (Near Field Communication) capabilities for seamless integration with devices. These improvements make it easier for users to carry and use their tokens, encouraging better adoption of secure authentication methods.
Security improvements in hardware OTP tokens have also focused on encryption and tamper resistance. Modern OTP tokens are equipped with advanced encryption algorithms that make it virtually impossible for hackers to intercept or replicate the one-time passwords generated. Additionally, tamper-resistant designs ensure that any attempt to physically alter or break into the token will disable its functionality, protecting the stored credentials. These features are especially important in industries where sensitive data, such as financial information or personal health records, must be kept secure.
The integration of hardware OTP tokens with cloud-based authentication platforms is another advancement that has improved their usability. These platforms allow businesses to manage and monitor multiple tokens, authenticate users remotely, and ensure compliance with security policies across different systems and devices. This cloud integration provides flexibility for companies that operate across multiple locations or have employees working remotely. Users can access secure networks from anywhere, and administrators can centrally manage token deployment, expiration, and replacement, simplifying the process of maintaining a secure authentication system.
Why Are Hardware OTP Tokens Critical for Enhancing Cybersecurity, Preventing Fraud, and Ensuring Compliance?
Hardware OTP tokens are critical for enhancing cybersecurity, preventing fraud, and ensuring compliance because they offer a strong, independent method of authentication that is resistant to many common cyberattack vectors. One of the primary benefits of OTP tokens is their ability to generate a unique password for each login session, which eliminates the risks associated with static passwords. Traditional passwords can be easily stolen through phishing attacks, keylogging malware, or database breaches, but an OTP token changes the password every time, making stolen credentials useless after a single use.This dynamic, time-sensitive approach to authentication is particularly valuable in preventing identity theft and fraud in industries like banking, where users need to access sensitive accounts securely. Financial institutions frequently use hardware OTP tokens to protect online banking transactions, ensuring that even if a user's account details are compromised, the attacker cannot complete a transaction without the one-time password generated by the token. This makes hardware OTP tokens a vital tool for reducing financial fraud and protecting user accounts.
In addition to protecting against cyberattacks, OTP tokens are critical for ensuring compliance with security regulations. Many industries, particularly healthcare, finance, and government, are subject to stringent data protection laws that require strong authentication methods to safeguard sensitive information. Regulations like the General Data Protection Regulation (GDPR) in Europe and the Health Insurance Portability and Accountability Act (HIPAA) in the United States mandate the use of secure methods to control access to private data. By implementing hardware OTP token authentication, organizations can meet these regulatory requirements and avoid costly fines or legal liabilities associated with data breaches.
OTP tokens also improve the security of remote work environments. As more companies adopt flexible work policies, the need to secure remote access to corporate networks and sensitive systems has become paramount. Hardware tokens provide a reliable way to ensure that only authorized users can access remote resources, reducing the risk of breaches caused by weak or compromised passwords. This is particularly important in industries where remote access to confidential information or critical infrastructure needs to be tightly controlled.
Furthermore, hardware OTP tokens offer an additional layer of security for privileged access management (PAM). PAM focuses on securing accounts with elevated permissions, such as system administrators or executives with access to sensitive data. These accounts are often the target of cyberattacks because of the higher level of access they provide. Using hardware OTP tokens to secure privileged accounts ensures that attackers cannot exploit stolen credentials to gain unauthorized access to critical systems.
What Factors Are Driving the Growth of the Hardware OTP Token Authentication Market?
Several key factors are driving the rapid growth of the hardware OTP token authentication market, including the increasing prevalence of cyberattacks, the rise of remote work, regulatory requirements for data protection, and advancements in authentication technology. First and foremost, the growing frequency of cyberattacks - such as phishing, ransomware, and identity theft - is pushing organizations to adopt stronger security measures. As attackers develop more sophisticated methods to steal credentials and infiltrate networks, businesses are turning to hardware OTP tokens as a reliable defense against these threats. The dynamic nature of OTPs makes it difficult for cybercriminals to exploit stolen credentials, significantly improving overall security.The shift toward remote work, accelerated by the COVID-19 pandemic, is another factor contributing to the growth of the OTP token market. With more employees working from home or accessing corporate systems remotely, companies are seeking secure ways to authenticate users and protect sensitive data. Hardware OTP tokens provide a robust solution for securing remote access, ensuring that only authorized individuals can log into corporate networks, even from outside the office. As remote work becomes a permanent part of many organizations' operations, the demand for secure authentication solutions like OTP tokens continues to rise.
Regulatory requirements are also driving the adoption of OTP token authentication. Industries that handle sensitive data, such as finance, healthcare, and government, are subject to strict regulations that mandate the use of strong authentication methods. For example, the Payment Card Industry Data Security Standard (PCI DSS) requires multi-factor authentication (MFA) for administrative access to cardholder data environments. By deploying hardware OTP tokens as part of an MFA strategy, organizations can ensure compliance with these regulations and reduce the risk of penalties for non-compliance.
Advancements in authentication technology are further contributing to the growth of the OTP token market. As hardware tokens become more compact, durable, and user-friendly, businesses and consumers alike are more likely to adopt them as a security solution. The development of tokens with additional features, such as biometric verification or integration with mobile devices via NFC or Bluetooth, enhances both security and convenience. These innovations are making OTP tokens more accessible and appealing to a wider range of users.
Additionally, the increasing awareness of the importance of digital security among consumers is helping to drive the demand for OTP tokens. As more people experience the consequences of cyberattacks, such as identity theft or data breaches, they are becoming more proactive about protecting their online accounts. OTP tokens offer a simple and effective way for individuals to secure their personal information, making them a popular choice for online banking, email, and social media accounts.
In conclusion, the growth of the hardware OTP token authentication market is driven by the increasing threat of cyberattacks, the rise of remote work, regulatory demands for stronger security measures, and technological advancements that enhance the functionality and usability of OTP tokens. As organizations and individuals seek more robust methods to protect sensitive data and ensure secure access to digital systems, hardware OTP tokens will remain a critical tool in the fight against cybercrime and unauthorized access.
Report Scope
The report analyzes the Hardware OTP Token Authentication market, presented in terms of market value (USD). The analysis covers the key segments and geographic regions outlined below.- Segments: Segment (Disconnected, Contactless, Connected); End-Use (Enterprise Security, BFSI, Government, Healthcare, Other End-Uses).
- Geographic Regions/Countries: World; United States; Canada; Japan; China; Europe (France; Germany; Italy; United Kingdom; and Rest of Europe); Asia-Pacific; Rest of World.
Key Insights:
- Market Growth: Understand the significant growth trajectory of the Disconnected Authentication segment, which is expected to reach US$281.9 Million by 2030 with a CAGR of 6.1%. The Contactless Authentication segment is also set to grow at 6.7% CAGR over the analysis period.
- Regional Analysis: Gain insights into the U.S. market, valued at $125.5 Million in 2024, and China, forecasted to grow at an impressive 5.8% CAGR to reach $101.2 Million by 2030. Discover growth trends in other key regions, including Japan, Canada, Germany, and the Asia-Pacific.
Why You Should Buy This Report:
- Detailed Market Analysis: Access a thorough analysis of the Global Hardware OTP Token Authentication Market, covering all major geographic regions and market segments.
- Competitive Insights: Get an overview of the competitive landscape, including the market presence of major players across different geographies.
- Future Trends and Drivers: Understand the key trends and drivers shaping the future of the Global Hardware OTP Token Authentication Market.
- Actionable Insights: Benefit from actionable insights that can help you identify new revenue opportunities and make strategic business decisions.
Key Questions Answered:
- How is the Global Hardware OTP Token Authentication Market expected to evolve by 2030?
- What are the main drivers and restraints affecting the market?
- Which market segments will grow the most over the forecast period?
- How will market shares for different regions and segments change by 2030?
- Who are the leading players in the market, and what are their prospects?
Report Features:
- Comprehensive Market Data: Independent analysis of annual sales and market forecasts in US$ Million from 2024 to 2030.
- In-Depth Regional Analysis: Detailed insights into key markets, including the U.S., China, Japan, Canada, Europe, Asia-Pacific, Latin America, Middle East, and Africa.
- Company Profiles: Coverage of players such as Deepnet Security, Dell Technologies, Entrust Datacard Corporation, FEITIAN Technologies Co., Ltd., Fortinet, Inc. and more.
- Complimentary Updates: Receive free report updates for one year to keep you informed of the latest market developments.
Some of the 12 companies featured in this Hardware OTP Token Authentication market report include:
- Deepnet Security
- Dell Technologies
- Entrust Datacard Corporation
- FEITIAN Technologies Co., Ltd.
- Fortinet, Inc.
- Gemalto NV
- HID Global Corporation
- ID Control
- Nexus AG
- Securemetric Technology Sdn. Bhd.
- SecuTech Solutions Pty Ltd.
- Symantec Corporation
- VASCO Data Security International, Inc.
- Yubico AB
This edition integrates the latest global trade and economic shifts into comprehensive market analysis. Key updates include:
- Tariff and Trade Impact: Insights into global tariff negotiations across 180+ countries, with analysis of supply chain turbulence, sourcing disruptions, and geographic realignment. Special focus on 2025 as a pivotal year for trade tensions, including updated perspectives on the Trump-era tariffs.
- Adjusted Forecasts and Analytics: Revised global and regional market forecasts through 2030, incorporating tariff effects, economic uncertainty, and structural changes in globalization. Includes historical analysis from 2015 to 2023.
- Strategic Market Dynamics: Evaluation of revised market prospects, regional outlooks, and key economic indicators such as population and urbanization trends.
- Innovation & Technology Trends: Latest developments in product and process innovation, emerging technologies, and key industry drivers shaping the competitive landscape.
- Competitive Intelligence: Updated global market share estimates for 2025, competitive positioning of major players (Strong/Active/Niche/Trivial), and refined focus on leading global brands and core players.
- Expert Insight & Commentary: Strategic analysis from economists, trade experts, and domain specialists to contextualize market shifts and identify emerging opportunities.
Table of Contents
Companies Mentioned (Partial List)
A selection of companies mentioned in this report includes, but is not limited to:
- Deepnet Security
- Dell Technologies
- Entrust Datacard Corporation
- FEITIAN Technologies Co., Ltd.
- Fortinet, Inc.
- Gemalto NV
- HID Global Corporation
- ID Control
- Nexus AG
- Securemetric Technology Sdn. Bhd.
- SecuTech Solutions Pty Ltd.
- Symantec Corporation
- VASCO Data Security International, Inc.
- Yubico AB
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 179 |
| Published | January 2026 |
| Forecast Period | 2024 - 2030 |
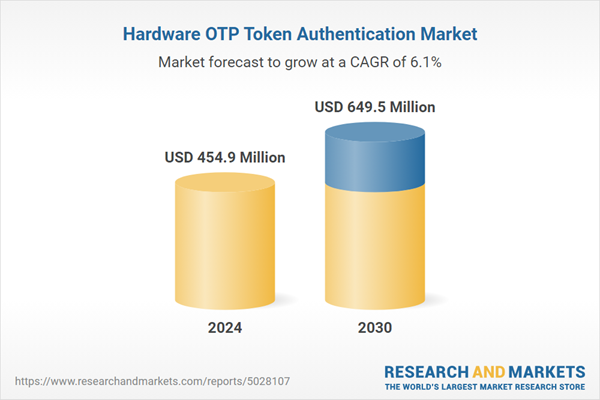
| Estimated Market Value ( USD | $ 454.9 Million |
| Forecasted Market Value ( USD | $ 649.5 Million |
| Compound Annual Growth Rate | 6.1% |
| Regions Covered | Global |