Enterprise Security is the fastest growing segment, North America is the largest market globally
Speak directly to the analyst to clarify any post sales queries you may have.
10% Free customizationThis report comes with 10% free customization, enabling you to add data that meets your specific business needs.
Key Market Drivers
The Global Hardware OTP Token Authentication Market is significantly propelled by the escalating frequency and sophistication of cybersecurity threats and the resulting concerns over data breaches. The relentless rise in cyberattacks mandates more robust and tamper-resistant authentication mechanisms, moving beyond traditional password-based security which remains highly vulnerable. For instance, according to IBM's 2024 Cost of a Data Breach Report, compromised credential attacks were identified as the leading cause of breaches, accounting for 16% of all incidents and incurring an average cost of $4.81 million per breach.Key Market Challenges
The relatively high initial investment required for large-scale hardware token deployments represents a significant impediment to the expansion of the Global Hardware OTP Token Authentication Market. This substantial upfront cost encompasses not only the procurement of individual tokens for an extensive user base but also the associated administrative overhead for their distribution, registration, and ongoing management. Such considerable financial outlay can deter organizations, particularly those with constrained budgets or extensive workforces, from adopting these solutions.Key Market Trends
The integration of biometric features in hardware tokens represents a significant evolutionary step for authentication solutions, moving beyond simple one-time password generation. This trend enhances both security and user convenience by embedding unique biological characteristics, such as fingerprints, directly into the authentication process. Instead of relying solely on a generated code, users can verify their identity with a touch, providing a highly phishing-resistant and user-friendly experience. According to the National Institute of Standards and Technology (NIST), in June 2024, updated guidance for federal contractors noted biometrics as a technology for identification and authentication, particularly for multi-factor authentication, underscoring its role in robust security frameworks.Key Market Players Profiled:
- One Identity LLC
- Entrust Corporation
- RSA Security LLC
- Thales Group
- SurePassID, Corp.
- HID Global Corporation
- IDEMIA Group
- OneSpan Inc.
- Yubico Group
- Deepnet Security
Report Scope:
In this report, the Global Hardware OTP Token Authentication Market has been segmented into the following categories:By Type:
- Connected
- Disconnected
- Contactless
By End User:
- BFSI
- Government
- Enterprise Security
- Others
By Region:
- North America
- Europe
- South America
- Middle East & Africa
- Asia Pacific
Competitive Landscape
Company Profiles: Detailed analysis of the major companies present in the Global Hardware OTP Token Authentication Market.Available Customizations:
With the given market data, the publisher offers customizations according to a company's specific needs. The following customization options are available for the report:- Detailed analysis and profiling of additional market players (up to five).
This product will be delivered within 1-3 business days.
Table of Contents
Companies Mentioned
- One Identity LLC
- Entrust Corporation
- RSA Security LLC
- Thales Group
- SurePassID, Corp.
- HID Global Corporation
- IDEMIA Group
- OneSpan Inc.
- Yubico Group
- Deepnet Security
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 185 |
| Published | November 2025 |
| Forecast Period | 2024 - 2030 |
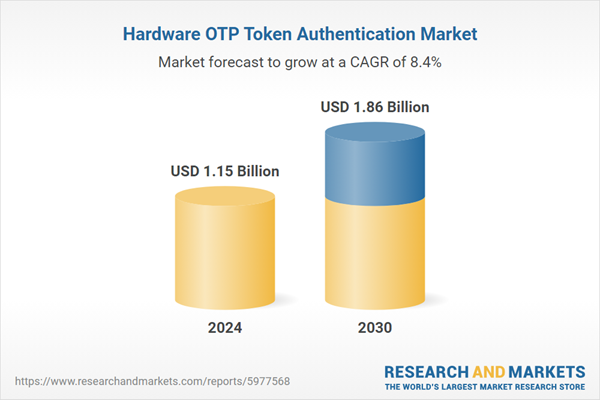
| Estimated Market Value ( USD | $ 1.15 Billion |
| Forecasted Market Value ( USD | $ 1.86 Billion |
| Compound Annual Growth Rate | 8.3% |
| Regions Covered | Global |
| No. of Companies Mentioned | 10 |