Global IAM Security Services Market - Key Trends and Drivers Summarized
Is Identity and Access Management (IAM) Security the Key to Protecting Digital Assets in the Age of Cyber Threats?
Identity and Access Management (IAM) security services are becoming indispensable in today's cybersecurity landscape, but why are they so critical for businesses managing digital identities and securing access to their systems? IAM security services enable organizations to define, enforce, and manage access policies across their IT infrastructure. These services ensure that the right individuals have appropriate access to the right resources at the right times, helping organizations safeguard sensitive data, comply with regulatory requirements, and mitigate security risks. IAM encompasses a broad range of solutions, including single sign-on (SSO), multi-factor authentication (MFA), privileged access management (PAM), identity governance, and more.The significance of IAM lies in its ability to provide robust security controls while ensuring operational efficiency. By automating access management and applying centralized policies, IAM security services reduce the likelihood of unauthorized access to sensitive systems, which is crucial in an era where cyberattacks are growing more frequent and sophisticated. As businesses increasingly shift to digital platforms, adopt cloud services, and enable remote workforces, IAM has emerged as a foundational component of enterprise security strategies. With IAM services, organizations can ensure that users, both internal and external, are authenticated securely and that their access is governed according to predefined policies, thus reducing the risks of breaches and insider threats.
How Have Technological Advancements Improved IAM Security Services for Better Access Control and Risk Management?
Technological advancements have dramatically enhanced Identity and Access Management (IAM) security services, making them more effective at controlling access, managing identities, and mitigating risks in complex IT environments. One of the most significant advancements is the integration of artificial intelligence (AI) and machine learning (ML) into IAM platforms. AI and ML enable predictive analytics, allowing organizations to monitor user behavior in real-time and detect anomalies that may indicate a security breach. For example, AI can flag unusual login attempts from unexpected locations or devices, automatically triggering additional authentication steps or locking accounts to prevent unauthorized access. This use of AI-driven risk scoring makes IAM services more dynamic, adapting security controls based on real-time risks rather than static rules.Cloud-based IAM services represent another major advancement, offering scalability, flexibility, and ease of deployment compared to traditional on-premises solutions. As organizations move more workloads to the cloud, cloud-native IAM platforms allow for seamless integration across cloud environments, enabling businesses to apply consistent access policies across multiple platforms, such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud. Cloud IAM services also simplify identity management by offering centralized control over all identities, applications, and data, regardless of whether they are hosted on-premises or in the cloud. This has become particularly important as businesses adopt multi-cloud and hybrid cloud strategies, which require sophisticated IAM systems to manage complex, distributed environments.
The rise of Zero Trust architecture has further improved IAM security services by reshaping how organizations approach access control. Zero Trust is a security model that assumes no user or device should be trusted by default, even if they are within the network perimeter. IAM solutions that support Zero Trust continuously verify user identities, device security, and context, ensuring that access is granted only when specific conditions are met. This continuous verification process minimizes the risks of lateral movement within a network, reducing the likelihood of an attacker gaining access to critical systems after compromising a single user account. With Zero Trust, IAM services shift from traditional perimeter-based security to a more granular, risk-based approach that significantly strengthens access control.
Multi-factor authentication (MFA) has also seen substantial improvements, making it easier for organizations to implement strong security controls without disrupting user experience. Modern IAM solutions offer flexible MFA options, including biometrics, hardware tokens, SMS-based codes, and mobile authentication apps, allowing organizations to choose the most appropriate authentication methods based on their security needs and user preferences. Adaptive MFA, which adjusts authentication requirements based on contextual factors such as user location or device security posture, has become more prevalent, helping to strike a balance between security and convenience. This ensures that high-risk access requests trigger additional security checks, while low-risk requests can proceed with minimal friction for the user.
IAM security services have also advanced in their ability to manage privileged access, which is critical for protecting sensitive data and systems from insider threats and external attackers. Privileged Access Management (PAM) solutions provide organizations with tools to control, monitor, and audit access to high-level accounts, such as system administrators and executives, which have elevated permissions. Modern PAM solutions integrate with IAM platforms, enabling organizations to enforce least-privilege access policies and limit the scope of what privileged users can do. In addition, session recording, real-time monitoring, and automated alerts ensure that any unusual activity by privileged users is immediately detected and addressed, further reducing the risk of breaches.
Single sign-on (SSO) solutions have also improved, offering seamless access across a variety of applications and platforms while maintaining strong security controls. SSO reduces the number of passwords users need to manage, decreasing the risk of password fatigue and reducing the likelihood of password-related security breaches. Additionally, modern SSO solutions leverage standards like SAML (Security Assertion Markup Language) and OAuth, allowing users to authenticate across diverse systems with a single identity. SSO integration with MFA and identity federation further strengthens security, ensuring that users can access multiple systems securely and efficiently.
Another advancement in IAM is the rise of identity governance and administration (IGA) solutions. IGA tools provide centralized management of user identities and access rights, enabling organizations to automate the provisioning and de-provisioning of user accounts based on roles, job functions, or regulatory requirements. Automated workflows ensure that new employees are granted access only to the resources they need, while former employees or contractors are promptly removed from the system, reducing the risk of orphaned accounts. This automation not only improves security by enforcing access control policies but also simplifies compliance with data protection regulations like GDPR, HIPAA, and CCPA, which require organizations to demonstrate effective control over who can access sensitive data.
Finally, the adoption of decentralized identity management through blockchain technology is gaining momentum in IAM. Decentralized identity solutions allow users to control their digital identities by storing authentication credentials in a blockchain network, rather than relying on a central authority. This ensures greater privacy and security for users, as their identities are not stored in centralized databases that could be vulnerable to breaches. Decentralized identity solutions also support self-sovereign identity (SSI), where users can independently verify and share their identity attributes without needing intermediaries. This technology is still emerging but holds significant potential for enhancing privacy and security in IAM.
Why Are IAM Security Services Critical for Access Control, Compliance, and Risk Management?
IAM security services are critical for access control, compliance, and risk management because they provide a centralized and automated system for managing who can access an organization's resources, what they can access, and under what circumstances. One of the primary reasons IAM is so essential for access control is its ability to enforce role-based access control (RBAC) and least-privilege principles. RBAC ensures that users only have access to the resources necessary to perform their job functions, reducing the risk of unauthorized access or accidental data exposure. Least-privilege access further minimizes risk by ensuring that even users with elevated permissions only have access to specific systems or data for the duration required to complete a task. IAM security services allow organizations to define these access rules centrally, applying them consistently across all applications and systems.For compliance, IAM security services play a crucial role in helping organizations meet regulatory requirements related to data privacy and security. Laws like the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and the California Consumer Privacy Act (CCPA) require organizations to control and monitor access to sensitive information. IAM solutions provide audit trails, real-time monitoring, and detailed reports on who accessed what resources and when, ensuring that organizations can demonstrate compliance during audits. These solutions also automate access reviews and certifications, ensuring that user permissions are regularly reviewed and adjusted to align with compliance mandates.
IAM services are also vital for risk management, particularly in the context of insider threats, cyberattacks, and data breaches. Insider threats, whether intentional or accidental, are a significant risk for many organizations. IAM security services mitigate this risk by monitoring user behavior, enforcing least-privilege access, and automatically deactivating accounts when an employee leaves the organization or changes roles. This reduces the likelihood of unauthorized access to sensitive data or systems. In the event of a cyberattack, IAM solutions provide strong authentication mechanisms such as MFA and continuous monitoring of login activity, making it more difficult for attackers to gain access using stolen credentials.
In a remote work environment, IAM security services are essential for controlling access to company resources from various locations and devices. As businesses adopt remote and hybrid work models, IAM solutions ensure that employees can securely access corporate applications and data regardless of their location. Adaptive authentication and conditional access policies, which adjust security measures based on contextual factors like user location or device health, are especially important in remote work scenarios. By verifying user identities dynamically and applying appropriate security controls, IAM services reduce the risk of unauthorized access while enabling a seamless experience for remote workers.
IAM services are also critical for managing third-party access, particularly for vendors, contractors, and partners who need temporary access to specific systems. Without proper controls in place, third-party access can expose organizations to security risks, including data breaches and compliance violations. IAM solutions enable businesses to create temporary or restricted access accounts for third-party users, ensuring that they only have access to the necessary resources for a specific time period. Automated de-provisioning and auditing capabilities ensure that these accounts are disabled once the project or contract ends, reducing the risk of orphaned accounts that could be exploited by attackers.
Single sign-on (SSO) and multi-factor authentication (MFA) are essential IAM services that enhance both access control and user experience. SSO reduces the need for users to manage multiple credentials, streamlining access to multiple applications while maintaining strong security standards. By integrating SSO with MFA, businesses can enforce secure authentication across all applications without requiring users to remember different passwords. This reduces the risk of password fatigue, password reuse, and phishing attacks. In industries where data security is paramount, such as healthcare, finance, and government, IAM services that combine SSO and MFA are critical for ensuring secure, compliant access to sensitive data and systems.
In addition to access control, IAM services support identity lifecycle management, which is crucial for ensuring that user accounts are properly managed throughout their lifecycle - from provisioning to de-provisioning. Identity lifecycle management ensures that new employees are granted access to the necessary resources quickly, while former employees, contractors, or temporary workers are removed from the system immediately upon departure. This reduces the risk of unauthorized access by ensuring that dormant or unused accounts are not left vulnerable to exploitation. Identity lifecycle management also helps organizations maintain compliance by ensuring that access controls are up-to-date and aligned with security policies and regulatory requirements.
What Factors Are Driving the Growth of the IAM Security Services Market?
Several factors are driving the rapid growth of the Identity and Access Management (IAM) security services market, including the increasing complexity of IT environments, the rise of cyber threats, the growing importance of compliance, and the shift to remote and hybrid work models. One of the primary drivers is the growing complexity of IT ecosystems, as organizations increasingly adopt cloud services, mobile devices, and remote work solutions. As businesses rely on a mix of on-premises, cloud, and third-party applications, IAM services are needed to provide centralized access control and identity management across all platforms. The ability to manage identities and access consistently across multiple environments is essential for ensuring security and operational efficiency in today's distributed IT landscapes.The rise of cyber threats, including phishing attacks, credential theft, and ransomware, is another significant factor contributing to the growth of the IAM market. With cyberattacks becoming more frequent and sophisticated, businesses are investing in IAM security services to protect their systems from unauthorized access and to mitigate the risk of breaches. The increased use of MFA, adaptive authentication, and identity governance solutions is a direct response to these threats, as organizations seek to strengthen their defenses and ensure that only authorized users can access critical resources.
Regulatory requirements related to data privacy and security are also driving the adoption of IAM services. Laws such as the GDPR, HIPAA, and CCPA require organizations to demonstrate control over who can access sensitive data, as well as to ensure that proper security measures are in place to protect personal information. IAM solutions help organizations meet these requirements by providing centralized access control, audit logs, and identity governance capabilities. As regulatory scrutiny continues to increase, especially around data protection, organizations are turning to IAM services to ensure compliance and avoid hefty fines.
The shift to remote work and the growing adoption of hybrid work models have further accelerated the need for IAM security services. With employees accessing company resources from various locations and devices, businesses need to ensure that access is secure and compliant with internal security policies. IAM solutions provide the tools needed to manage remote access securely, including adaptive authentication, conditional access policies, and mobile identity management. As more organizations adopt permanent remote or hybrid work policies, the demand for IAM services is expected to grow.
The increasing reliance on cloud-based applications and services is also driving demand for IAM solutions. As businesses move more workloads to the cloud, they need IAM services to manage access across multiple cloud platforms while ensuring compliance with security and regulatory standards. Cloud-based IAM services offer scalability, flexibility, and ease of deployment, making them an attractive option for organizations that need to manage identities and access in dynamic, multi-cloud environments. Additionally, the growing use of SaaS applications, which often require strong identity verification and access controls, is further boosting the adoption of cloud-native IAM solutions.
Cost efficiency is another factor driving the growth of the IAM security services market. By automating identity management and access control processes, IAM solutions help organizations reduce the operational costs associated with manual provisioning, de-provisioning, and access reviews. IAM services also reduce the risk of costly data breaches by ensuring that access policies are enforced consistently and that security controls are applied to all users. As businesses look to streamline their security operations while maintaining strong defenses, IAM services offer a cost-effective solution that reduces complexity and improves security posture.
The increasing use of AI and machine learning in IAM is also contributing to market growth. AI-driven IAM solutions enable organizations to automate threat detection, risk scoring, and access decision-making based on real-time analysis of user behavior. This level of automation not only improves security but also enhances user experience by reducing the need for manual interventions and simplifying access management. As AI and machine learning technologies continue to evolve, their integration into IAM platforms will likely drive further growth and innovation in the market.
With the growing complexity of IT environments, the rise of cyber threats, increasing regulatory requirements, and the shift to remote work, the IAM security services market is poised for continued growth. As organizations seek to strengthen their security posture, ensure compliance, and manage identities across distributed environments, IAM services will play an increasingly critical role in safeguarding digital assets and enabling secure, efficient operations across industries.
Report Scope
The report analyzes the IAM Security Services market, presented in terms of market value (USD). The analysis covers the key segments and geographic regions outlined below.- Segments: Component (Solutions, Services); Organization Size (Large Enterprises, SMEs); Vertical (BFSI, Travel & Hospitality, Healthcare, Retail & eCommerce, IT & ITeS, Education, Other Verticals).
- Geographic Regions/Countries: World; United States; Canada; Japan; China; Europe (France; Germany; Italy; United Kingdom; and Rest of Europe); Asia-Pacific; Rest of World.
Key Insights:
- Market Growth: Understand the significant growth trajectory of the Solutions Component segment, which is expected to reach US$34.8 Billion by 2030 with a CAGR of 12.4%. The Services Component segment is also set to grow at 14.9% CAGR over the analysis period.
- Regional Analysis: Gain insights into the U.S. market, valued at $6.7 Billion in 2024, and China, forecasted to grow at an impressive 12.5% CAGR to reach $7.9 Billion by 2030. Discover growth trends in other key regions, including Japan, Canada, Germany, and the Asia-Pacific.
Why You Should Buy This Report:
- Detailed Market Analysis: Access a thorough analysis of the Global IAM Security Services Market, covering all major geographic regions and market segments.
- Competitive Insights: Get an overview of the competitive landscape, including the market presence of major players across different geographies.
- Future Trends and Drivers: Understand the key trends and drivers shaping the future of the Global IAM Security Services Market.
- Actionable Insights: Benefit from actionable insights that can help you identify new revenue opportunities and make strategic business decisions.
Key Questions Answered:
- How is the Global IAM Security Services Market expected to evolve by 2030?
- What are the main drivers and restraints affecting the market?
- Which market segments will grow the most over the forecast period?
- How will market shares for different regions and segments change by 2030?
- Who are the leading players in the market, and what are their prospects?
Report Features:
- Comprehensive Market Data: Independent analysis of annual sales and market forecasts in US$ Million from 2024 to 2030.
- In-Depth Regional Analysis: Detailed insights into key markets, including the U.S., China, Japan, Canada, Europe, Asia-Pacific, Latin America, Middle East, and Africa.
- Company Profiles: Coverage of players such as Amazon Web Services, Inc., CA Technologies, Inc., Centrify Corporation, HID Global Corporation, IBM Corporation and more.
- Complimentary Updates: Receive free report updates for one year to keep you informed of the latest market developments.
Some of the 12 companies featured in this IAM Security Services market report include:
- Amazon Web Services, Inc.
- CA Technologies, Inc.
- Centrify Corporation
- HID Global Corporation
- IBM Corporation
- Microsoft Corporation
- NetIQ Corporation
- Okta, Inc.
- Oracle Corporation
- SailPoint Technologies Holdings, Inc.
- Symantec Corporation
This edition integrates the latest global trade and economic shifts into comprehensive market analysis. Key updates include:
- Tariff and Trade Impact: Insights into global tariff negotiations across 180+ countries, with analysis of supply chain turbulence, sourcing disruptions, and geographic realignment. Special focus on 2025 as a pivotal year for trade tensions, including updated perspectives on the Trump-era tariffs.
- Adjusted Forecasts and Analytics: Revised global and regional market forecasts through 2030, incorporating tariff effects, economic uncertainty, and structural changes in globalization. Includes historical analysis from 2015 to 2023.
- Strategic Market Dynamics: Evaluation of revised market prospects, regional outlooks, and key economic indicators such as population and urbanization trends.
- Innovation & Technology Trends: Latest developments in product and process innovation, emerging technologies, and key industry drivers shaping the competitive landscape.
- Competitive Intelligence: Updated global market share estimates for 2025, competitive positioning of major players (Strong/Active/Niche/Trivial), and refined focus on leading global brands and core players.
- Expert Insight & Commentary: Strategic analysis from economists, trade experts, and domain specialists to contextualize market shifts and identify emerging opportunities.
Table of Contents
Companies Mentioned (Partial List)
A selection of companies mentioned in this report includes, but is not limited to:
- Amazon Web Services, Inc.
- CA Technologies, Inc.
- Centrify Corporation
- HID Global Corporation
- IBM Corporation
- Microsoft Corporation
- NetIQ Corporation
- Okta, Inc.
- Oracle Corporation
- SailPoint Technologies Holdings, Inc.
- Symantec Corporation
Table Information
| Report Attribute | Details |
|---|---|
| No. of Pages | 179 |
| Published | January 2026 |
| Forecast Period | 2024 - 2030 |
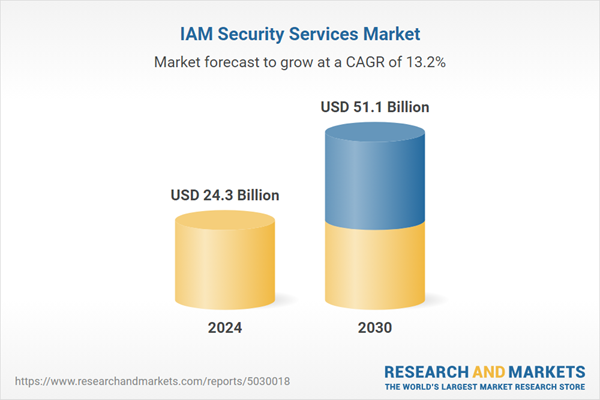
| Estimated Market Value ( USD | $ 24.3 Billion |
| Forecasted Market Value ( USD | $ 51.1 Billion |
| Compound Annual Growth Rate | 13.2% |
| Regions Covered | Global |